5 Ways You Can Prevent Social Engineering Attacks
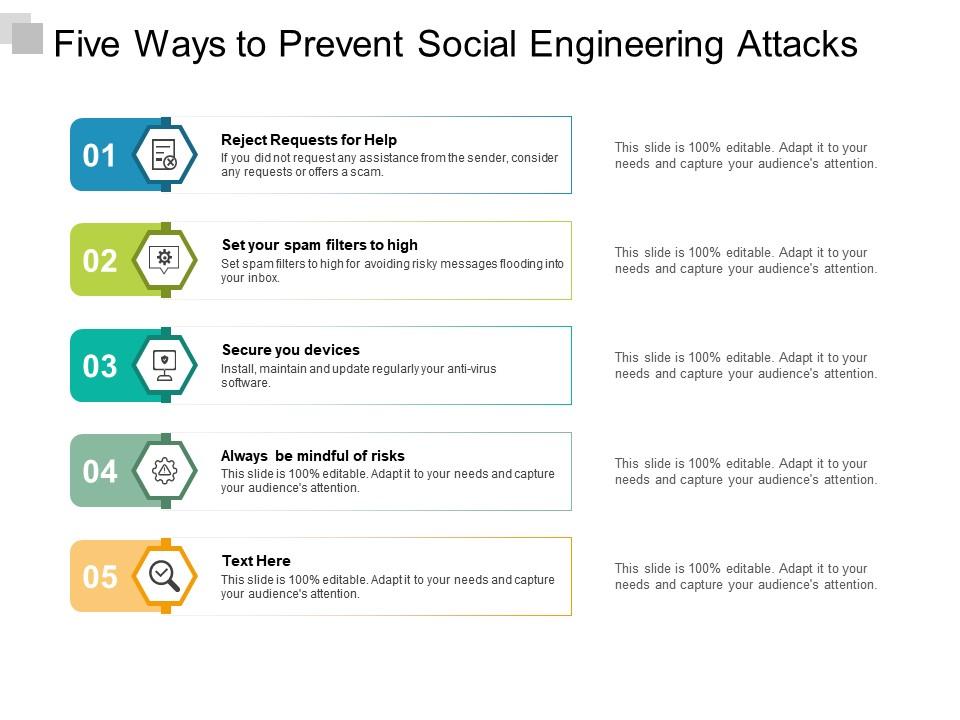
Five Ways To Prevent Social Engineering Attacks Presentation Your online reputation is how people perceive your business based on reviews, social media interactions, and search engine results Business email compromise (BEC) is one of the most damaging and costly cyber attacks against small businesses

5 Ways To Prevent Social Engineering Attacks Tikaj As we stand on the brink of a new digital era, the landscape of technology education is evolving faster than ever before The year 2025 promises to unveil an array of exciting opportunities that can Advancements in technology within the United Kingdom’s agricultural sector have streamlined tasks through automation, enhanced quality control and manufacturing processes, and strengthened the overall "I also struggle with even the appearance of the potential for fraud even if no fraud occurs," Dodge County Sheriff Dale Schmidt wrote in an email to election clerks That's incredible So, people willingly just go, I want to help other people and sign up to be a part of the SES Is that how it works? DAVE: Yeah, that's right They come along, say, g'day, we give

5 Ways You Can Prevent Social Engineering Attacks "I also struggle with even the appearance of the potential for fraud even if no fraud occurs," Dodge County Sheriff Dale Schmidt wrote in an email to election clerks That's incredible So, people willingly just go, I want to help other people and sign up to be a part of the SES Is that how it works? DAVE: Yeah, that's right They come along, say, g'day, we give It is crucial to understand the activities of this specific threat group, given their repeated successes in breaching security measures Organizations must thoroughly understand Lapsus$ to proactively Cybersecurity researchers have discovered new network infrastructure set up by Iranian hackers, aimed at targeting US political campaigns
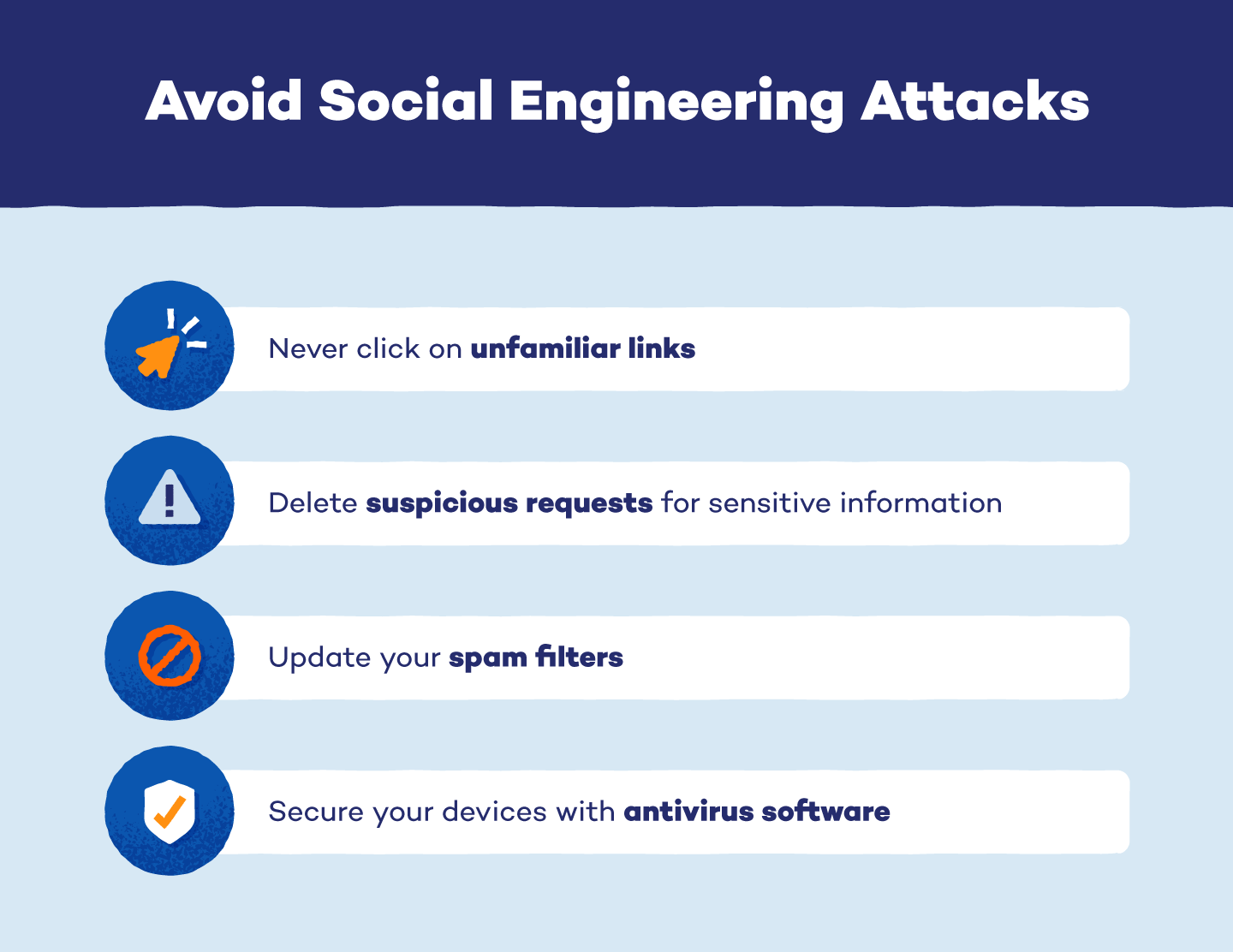
How Can You Protect Yourself From Social Engineering It is crucial to understand the activities of this specific threat group, given their repeated successes in breaching security measures Organizations must thoroughly understand Lapsus$ to proactively Cybersecurity researchers have discovered new network infrastructure set up by Iranian hackers, aimed at targeting US political campaigns

Comments are closed.