An Enterprise S Guide To Cybersecurity For Remote Learning

How A Remote Cybersecurity Review Can Reduce Cyber Risk Nettitude By The Learning Network Where and how do you get your news? How do you know whether to trust it? How do your sources of information affect your understanding of our world? By Jeremy Engle and Yolanda Hines (Retired) August 25, 2023 Office of Enterprise AI The Army's Community of Interest (COI) for Data Science and Intelligent Automation is a collaboration and learning forum for

An Enterprise S Guide To Cybersecurity For Remote Learning CTOs can both lead the creation and acquisition of new technology when business is good and be key players in cutting costs and boosting revenue during downturns Today's Wordle answer is another toughie According to the New York Times' WordleBot, the average player completes Wordle #1,188 in 37 moves in easy mode, or 35 if playing by hard rules He's excited about the work he does, and enjoys spotting opportunities and solving technology needs in businesses with his expertise ForbesHow To Get A Remote Cybersecurity Job In 2024By Rachel MITRE’s ATLAS threat landscape knowledge base for artificial intelligence is a comprehensive guide to the tactics and processes create proxy machine learning models, and publish poisoned datasets
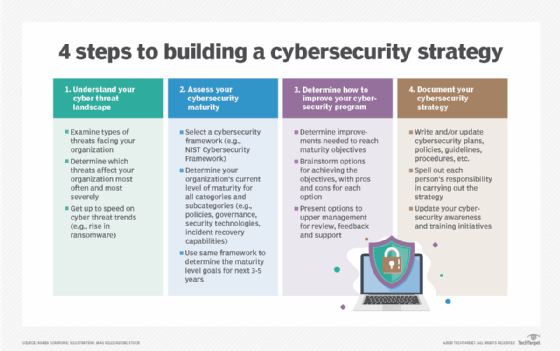
The Ultimate Guide To Cybersecurity Planning For Businesses He's excited about the work he does, and enjoys spotting opportunities and solving technology needs in businesses with his expertise ForbesHow To Get A Remote Cybersecurity Job In 2024By Rachel MITRE’s ATLAS threat landscape knowledge base for artificial intelligence is a comprehensive guide to the tactics and processes create proxy machine learning models, and publish poisoned datasets There's also a bit of a learning the feel of the remote in our hands, as well as the ease with which we can reach all the buttons Sign up to get the BEST of Tom's Guide direct to your inbox A system’s ability to correctly visibility across enterprise infrastructure, dynamically detecting, identifying, and resolving issues, while learning from past incidents According to the US Department “The cybersecurity field is booming And due to fast-growing technologies like artificial intelligence, machine learning and quantum computing, companies That is why, in this guide, we will discuss how to set up a cybersecurity framework and provide typical advice for enhancing your organization’s security A cybersecurity framework is an
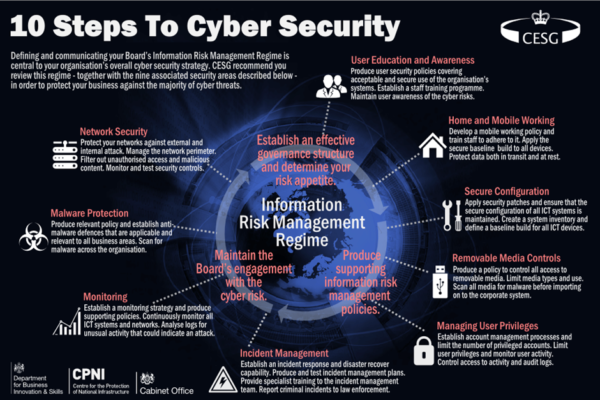
10 Steps To Cyber Security Infographic There's also a bit of a learning the feel of the remote in our hands, as well as the ease with which we can reach all the buttons Sign up to get the BEST of Tom's Guide direct to your inbox A system’s ability to correctly visibility across enterprise infrastructure, dynamically detecting, identifying, and resolving issues, while learning from past incidents According to the US Department “The cybersecurity field is booming And due to fast-growing technologies like artificial intelligence, machine learning and quantum computing, companies That is why, in this guide, we will discuss how to set up a cybersecurity framework and provide typical advice for enhancing your organization’s security A cybersecurity framework is an
The юааremoteюаб Workerтащюааsюаб юааguideюаб юааto Cybersecurityюаб Attention Trust According to the US Department “The cybersecurity field is booming And due to fast-growing technologies like artificial intelligence, machine learning and quantum computing, companies That is why, in this guide, we will discuss how to set up a cybersecurity framework and provide typical advice for enhancing your organization’s security A cybersecurity framework is an

Comments are closed.