Buffer Overflow On Stack Memory Overwrite Rip Alteration A Visual

Buffer Overflow On Stack Memory Overwrite Rip Alteration A Visual Buffer overflow: a vulnerability that exists within a code, that has no failsafe when arguments supplied to the program are bigger in size than allocated. in. When a program tries to put more data in a buffer, it overwrites the adjacent memory locations and thus, results in a crash. this is known as buffer overflow. mere overflowing a buffer and making.
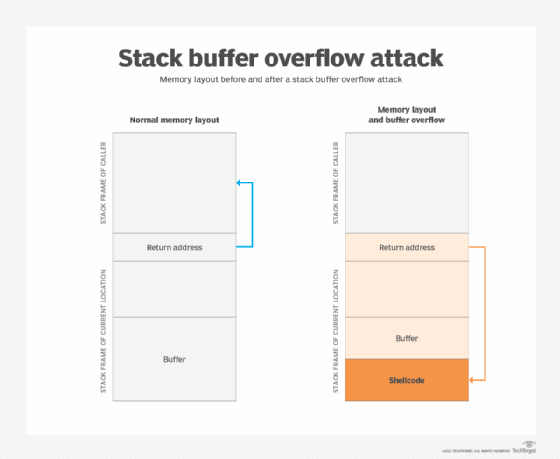
What Is A Buffer Overflow How Do These Types Of Attacks Work The reason the rip was not overflowed (technically it was, as we saw in the above screenshot, but there's more to it), is because the aaaaaaaa (0x4141414141414141) is considered a non canonical memory address, or, in other words, 0x4141414141414141 is a 64 bit wide address and current cpus prevent applications and oses to use 64 bit wide addresses. Which means, if the top of the stack is at say 100, then the stack grows towards 0, and reaching 0 is considered the end of stack and you know, you are out of memory. stacks works in a last in. 1. memory overwrite is often caused by dangling pointers. while this is not the only case, it's quite common and so i've found one technique that's pretty useful: by implementing your own memory allocator you can turn on a special debug mode where you write some known pattern into freed memory. you then periodically check all free memory to see. The stack is a fundamental data structure in computer memory used for storing temporary data during the execution of a program. it operates on a “last in first out” (lifo) basis, where the last item pushed into the stack is the first one to be popped out. the stack is vital for managing function calls and local variables in programs.
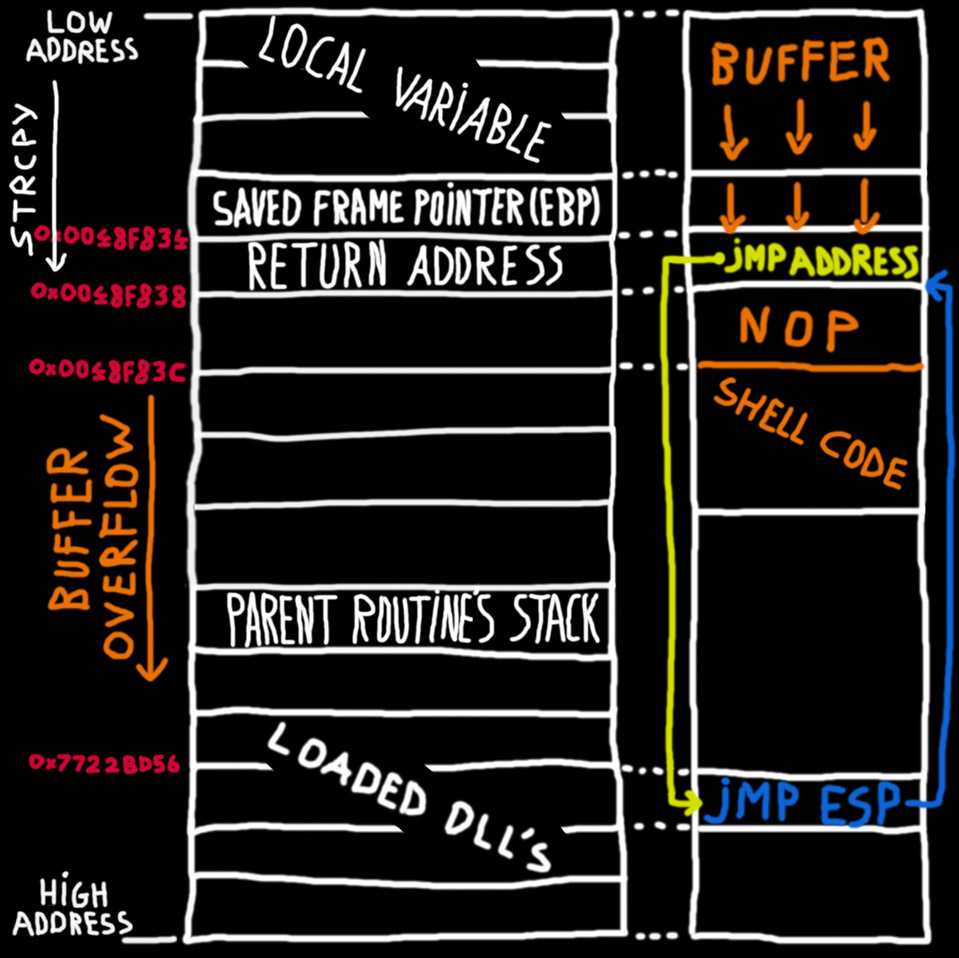
Buffer Overflow Explained 1. memory overwrite is often caused by dangling pointers. while this is not the only case, it's quite common and so i've found one technique that's pretty useful: by implementing your own memory allocator you can turn on a special debug mode where you write some known pattern into freed memory. you then periodically check all free memory to see. The stack is a fundamental data structure in computer memory used for storing temporary data during the execution of a program. it operates on a “last in first out” (lifo) basis, where the last item pushed into the stack is the first one to be popped out. the stack is vital for managing function calls and local variables in programs. Now, lets create a scaffold for our exploit, using pwntools and python: from pwn import * io = process(‘. caf’) print(io.recvregex(b’:’)) # read until we get. Stack buffer overflow. in software, a stack buffer overflow or stack buffer overrun occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed length buffer. [1][2] stack buffer overflow bugs are caused when a program writes more data to a buffer located on the.

If The Stack Grows Downwards How Can A Buffer Overflow Overwrite Now, lets create a scaffold for our exploit, using pwntools and python: from pwn import * io = process(‘. caf’) print(io.recvregex(b’:’)) # read until we get. Stack buffer overflow. in software, a stack buffer overflow or stack buffer overrun occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed length buffer. [1][2] stack buffer overflow bugs are caused when a program writes more data to a buffer located on the.

Comments are closed.