Common Types Of Cybersecurity Attacks
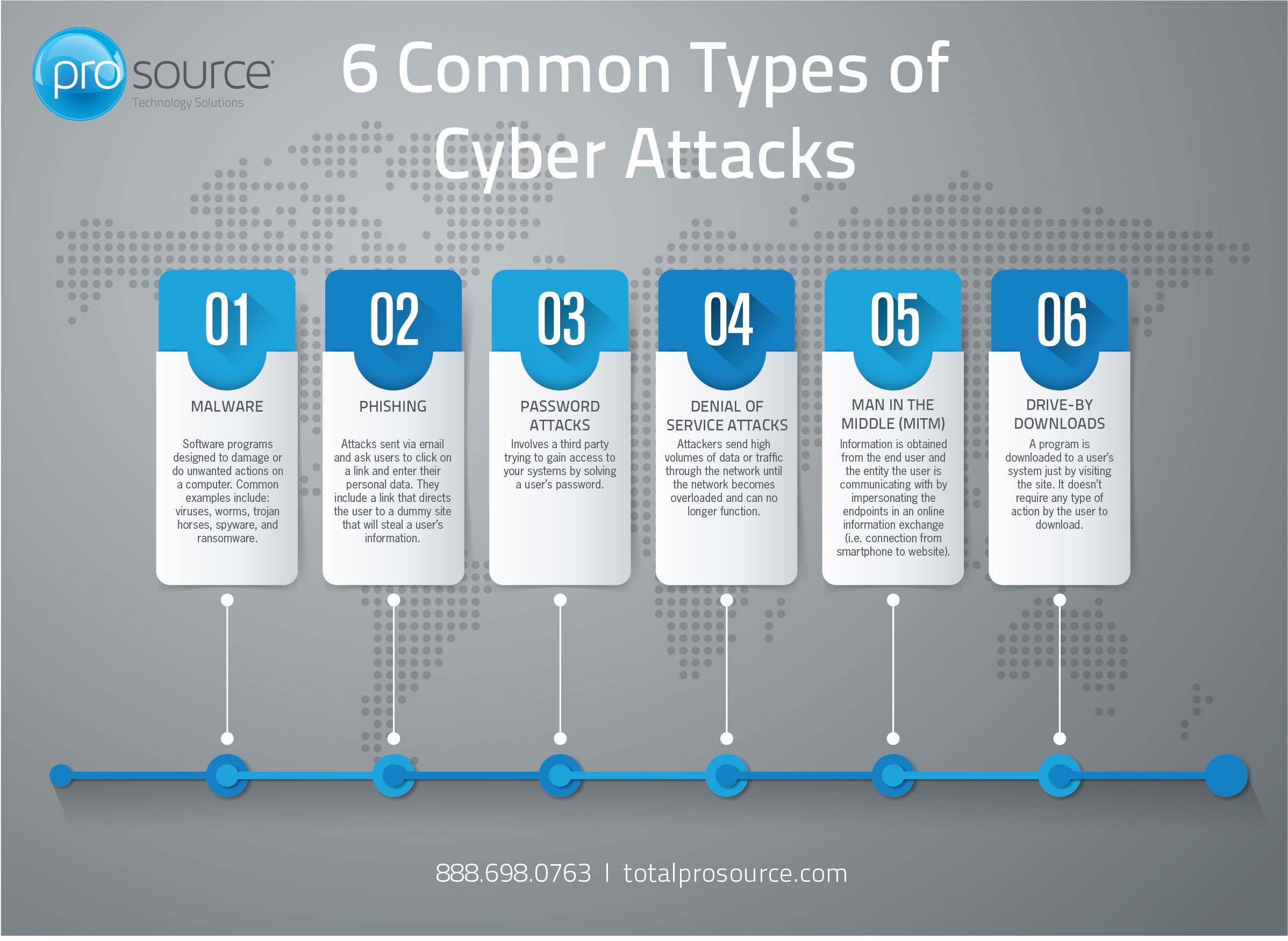
6 Common Types Of Cyber Attacks 1. malware. malware — or malicious software — is any program or code that is created with the intent to do harm to a computer, network or server. malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any. Top 20 most common types of cybersecurity attacks. 1. dos and ddos attacks. a denial of service (dos) attack is designed to overwhelm the resources of a system to the point where it is unable to reply to legitimate service requests. a distributed denial of service (ddos) attack is similar in that it also seeks to drain the resources of a system.

14 Most Common Types Of Cyber Attacks And How To Prevent Them 4. backdoor trojan. backdoor trojan attacks involve malicious programs that can deceptively install malware or data and open up what’s referred to as the “backdoor” to your computer system. when attackers gain access to the backdoor, they can hijack the device without it being known to the user. 5. The 17 most common types of cyber attacks. 1. malware based attacks (ransomware, trojans, etc.) malware refers to “malicious software” that is designed to disrupt or steal data from a computer network or server. hackers trick you into installing malware on your devices. Denial of service attack. a denial of service attack floods systems, servers, or networks with traffic to exhaust resources and bandwidth. as a result, the system is unable to fulfill legitimate requests. attackers can also use multiple compromised devices to launch this attack. this is known as a distributed denial of service (ddos) attack. Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing.
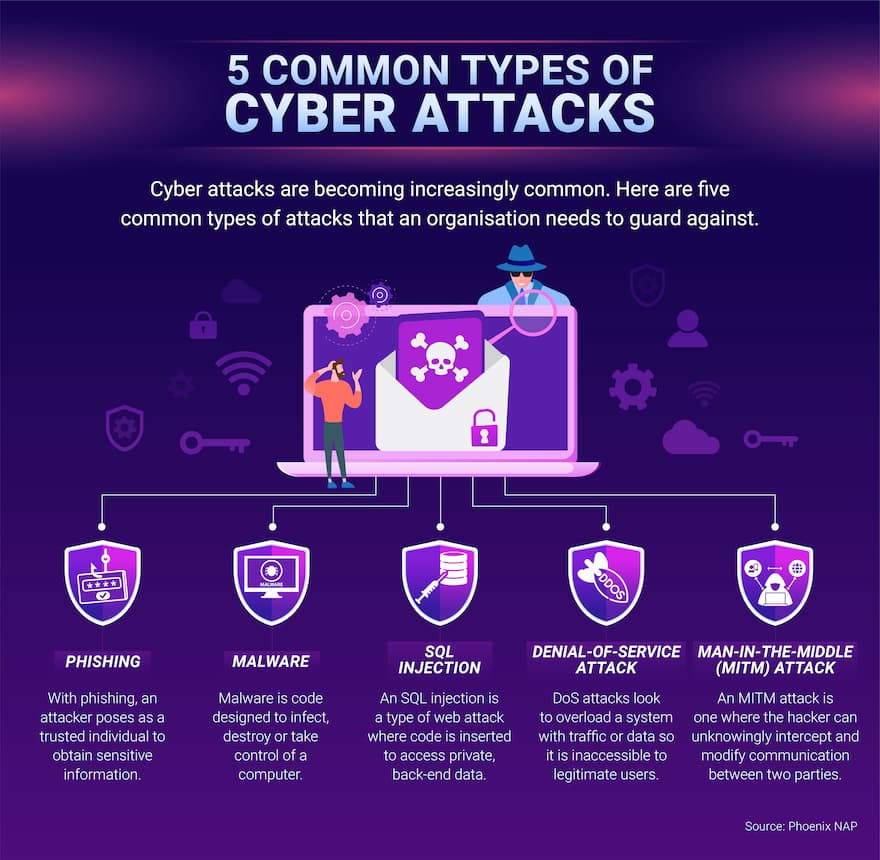
Cyber Attacks Tips For Protecting Your Organisation Ecu Online Denial of service attack. a denial of service attack floods systems, servers, or networks with traffic to exhaust resources and bandwidth. as a result, the system is unable to fulfill legitimate requests. attackers can also use multiple compromised devices to launch this attack. this is known as a distributed denial of service (ddos) attack. Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing. This article describes the 12 most common cyber threats today and provides cyber attack examples. 1. denial of service (dos) and distributed denial of service (ddos) attacks. both denial of service and distributed denial of service attacks are malicious attempts to make a server, service or network resource unavailable to its intended users. Damages are estimated in the billions to tens of billions of dollars globally. the attack ended when a cybersecurity researcher discovered a kill switch in the ransomware code. 3. denial of service (dos) attacks. dos attacks overload a computer system with excessive traffic, making it unavailable to users.

Things You Need To Know About Cyber Attacks Threats Risks Ecosystm This article describes the 12 most common cyber threats today and provides cyber attack examples. 1. denial of service (dos) and distributed denial of service (ddos) attacks. both denial of service and distributed denial of service attacks are malicious attempts to make a server, service or network resource unavailable to its intended users. Damages are estimated in the billions to tens of billions of dollars globally. the attack ended when a cybersecurity researcher discovered a kill switch in the ransomware code. 3. denial of service (dos) attacks. dos attacks overload a computer system with excessive traffic, making it unavailable to users.
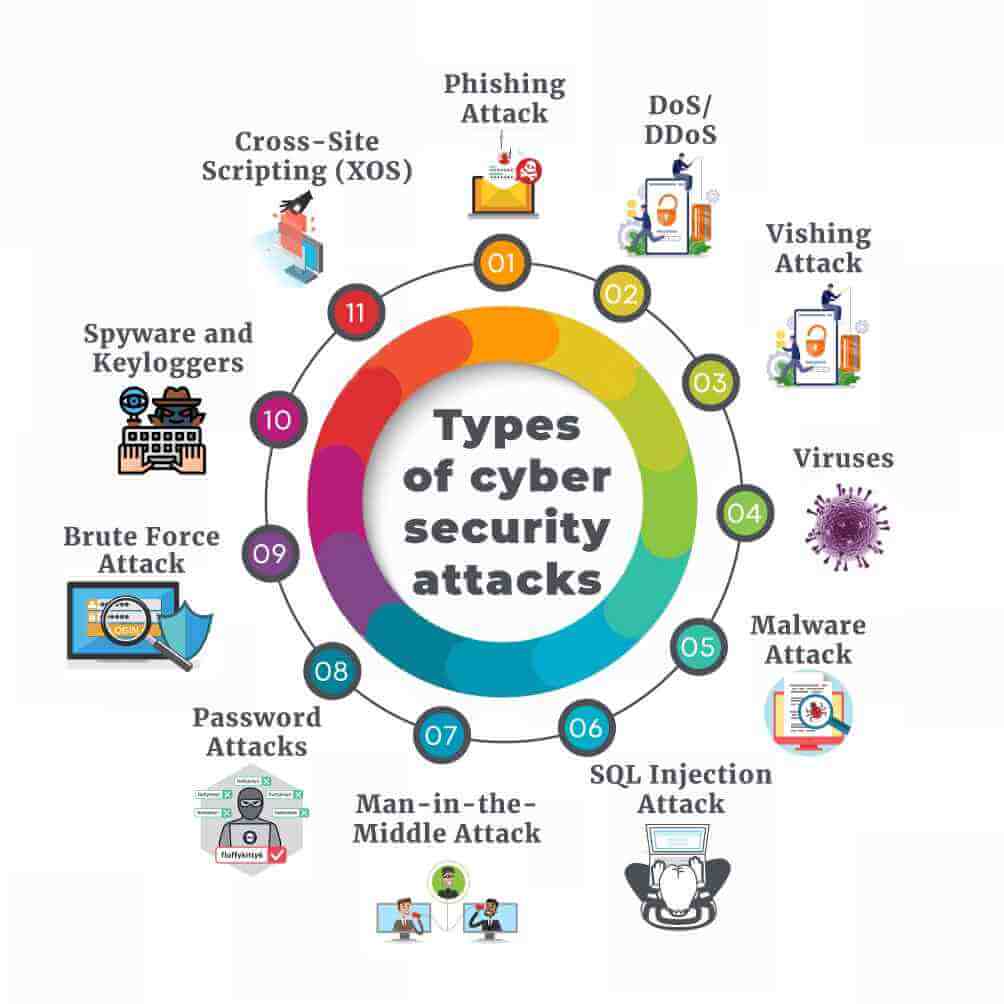
A Comprehensive Study Of Cyber Security And Its Types

Comments are closed.