Cybersecurity Social Engineering Explained

Cybersecurity Social Engineering Explained Eventura Explore the essential roles of Red vs Blue teams in cybersecurity Learn how their collaboration strengthens defenses against evolving cyber threats Whale phishing involves targeting wealthy or influential individuals through personalised phishing messages crafted after thorough research Attackers
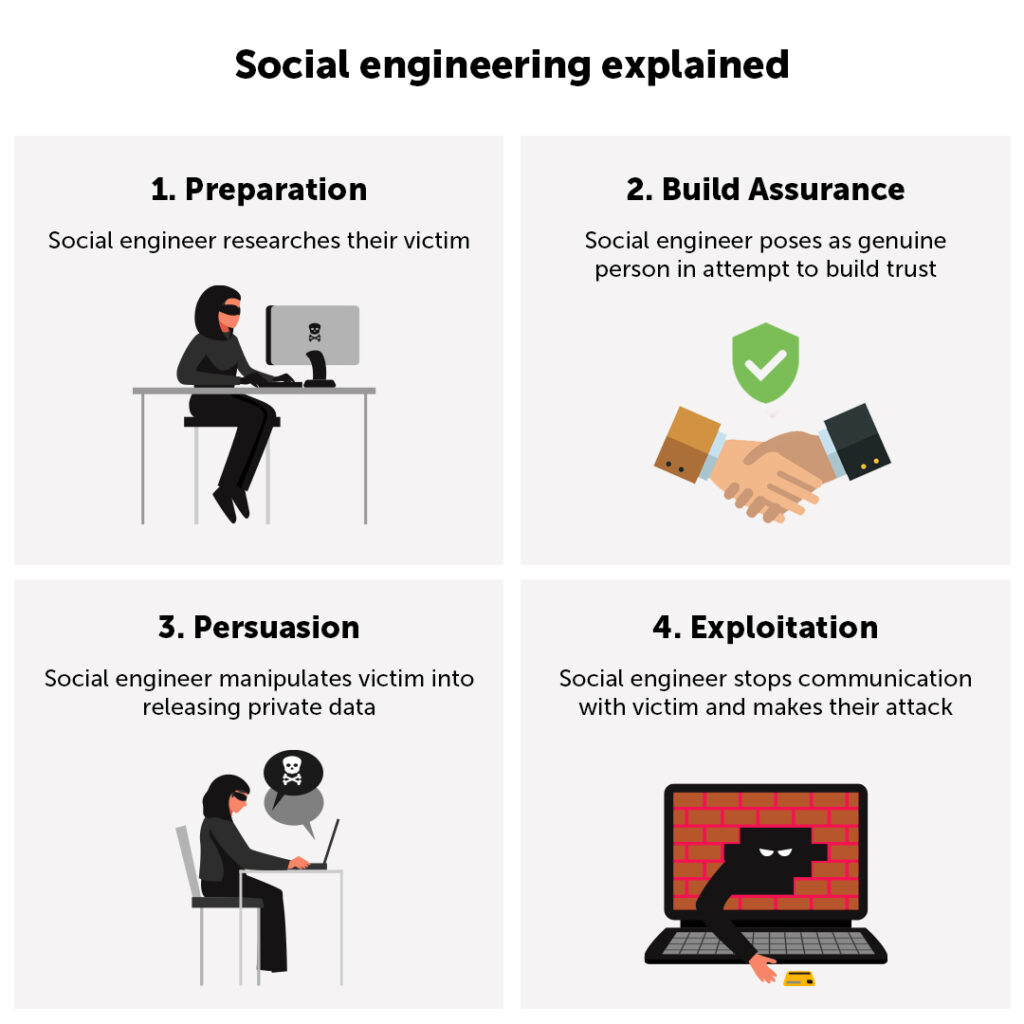
What Is Social Engineering Do You Know The Red Flags Understanding The Zero-Trust Model Zero trust is nothing but a security architecture that enforces strict verification for every user and device that is trying to access company IBM's Chris Hockings predicts a safer internet with advances in passkey tech, digital identity, deepfake defenses, and post-quantum cryptography In an era where digital transformation is integral to business success, cybersecurity has become a pivotal issue for organisations of all sizes As cyberthreats become more sophisticated, companies Hackers bypass MFA using techniques like token theft, malware and social engineering Learn how to defend your accounts effectively and avoid common pitfalls

What Is Social Engineering In Cyber Security Explained Youtube In an era where digital transformation is integral to business success, cybersecurity has become a pivotal issue for organisations of all sizes As cyberthreats become more sophisticated, companies Hackers bypass MFA using techniques like token theft, malware and social engineering Learn how to defend your accounts effectively and avoid common pitfalls The conference, organized through a collaboration between Generative AI for Good and the 8200 Alumni Association and hosted by graduate of the Gesher Leadership Program and journalist Noa Lavie, Australian banks and government are not rushing to adopt passkey authentication methods, despite the added security benefits Learn why they lag in embracing this crucial technology Cybersecurity experts have advised businesses in Nigeria to brace for an uptick in cybercrime activities that usually characterise the ember At least eight people were killed and nearly 3,000 wounded when pagers used by Hezbollah members - including fighters and medics - detonated simultaneously across Lebanon

Comments are closed.