Electronics Free Full Text Data Integrity Preservation Schemes In
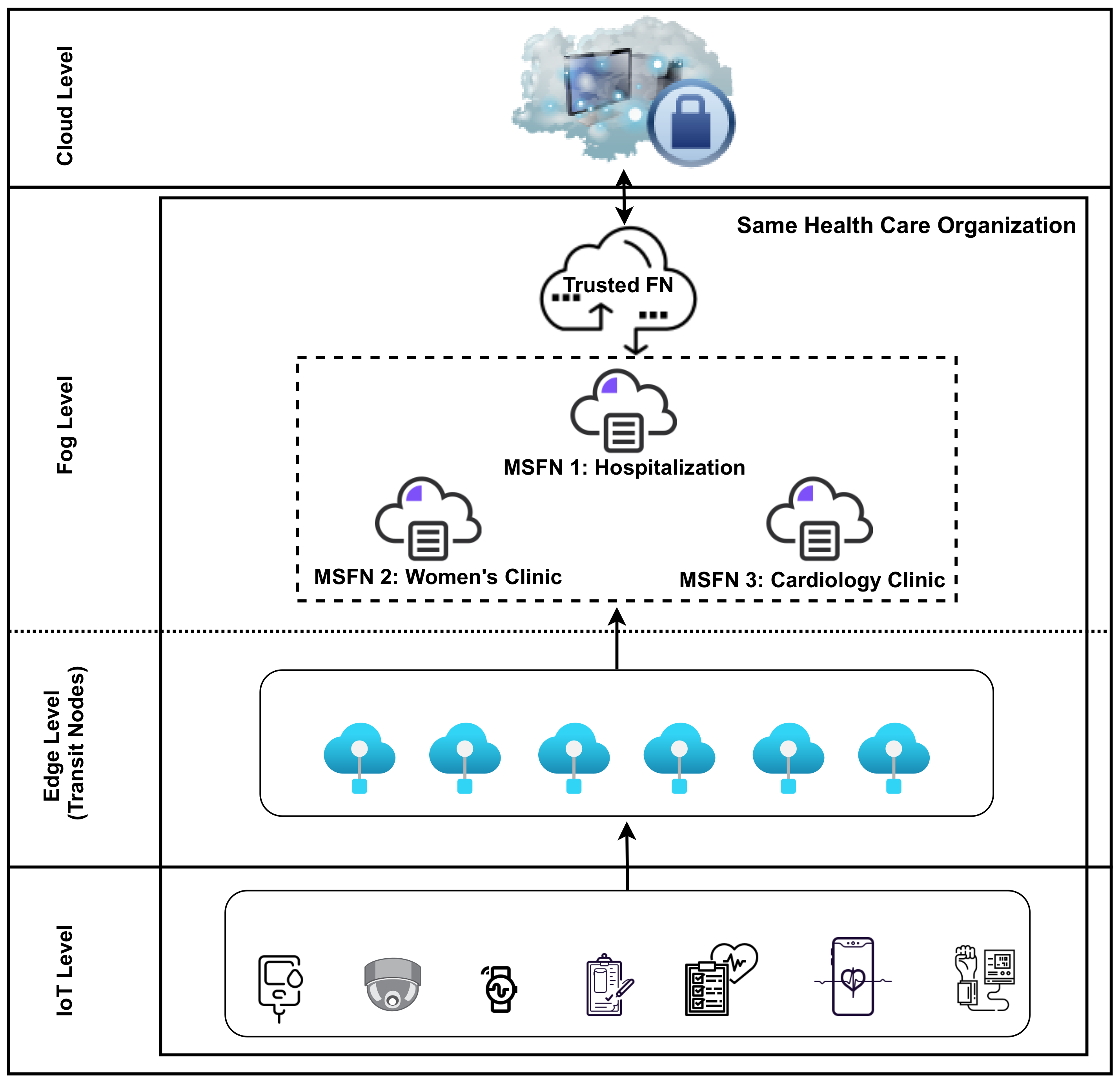
Electronics Free Full Text Data Integrity Preservation Schemes In The volume of data generated worldwide is rapidly growing. cloud computing, fog computing, and the internet of things (iot) technologies have been adapted to compute and process this high data volume. in coming years information technology will enable extensive developments in the field of healthcare and offer health care providers and patients broadened opportunities to enhance their. Search text. search type . add circle outline "data integrity preservation schemes in smart healthcare systems that use fog computing distribution" electronics 10.

Electronics Free Full Text Data Integrity Preservation Schemes In The work proposes a blockchain based anonymous authentication and integrity preservation scheme for secure communication in vehicular ad hoc networks (vanets) called baiv. the paper starts with an introduction about the topic and provides a comprehensive state of the art section. In 2020, zhao et al. [18] utilized blockchain technology for providing privacy for remote data with the support of an integrity verification approach in the information management systems of the. Specifically, an efficient pseudonym identity based privacy preserving report approach is proposed for the control center to obtain the fine grained usage data of all the users while protecting user's privacy. an online off line hash tree based mechanism is also designed to check and assure data integrity of communications. because of the. A growing number of medical records are changed by the electronic folders that can be shared and transmitted in real time in recent years as a result of the speedy improvement of data mechanisms and network methodologies. yet, security breaches and privacy issues could affect medical data sent over open communication channels. due to its distinctive qualities including immutability, blockchain.
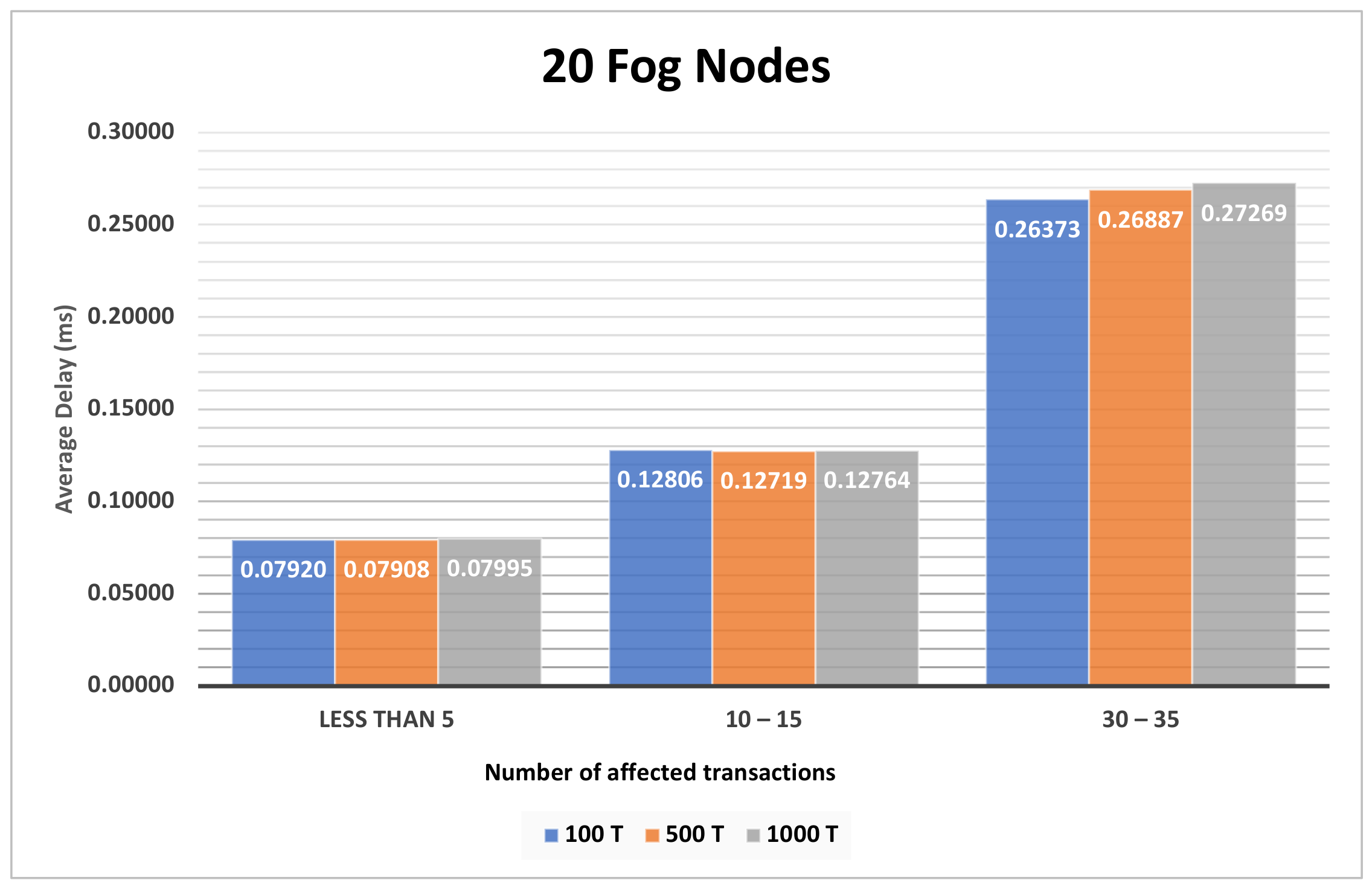
Electronics Free Full Text Data Integrity Preservation Schemes In Specifically, an efficient pseudonym identity based privacy preserving report approach is proposed for the control center to obtain the fine grained usage data of all the users while protecting user's privacy. an online off line hash tree based mechanism is also designed to check and assure data integrity of communications. because of the. A growing number of medical records are changed by the electronic folders that can be shared and transmitted in real time in recent years as a result of the speedy improvement of data mechanisms and network methodologies. yet, security breaches and privacy issues could affect medical data sent over open communication channels. due to its distinctive qualities including immutability, blockchain. In this chapter, we will introduce a novel secure data aggregation scheme to achieve privacy preservation and data integrity with differential privacy and fault tolerance (bao and lu, peer to peer. To design an efficient and secure data aggregation scheme fitting real applications has been pursued by research communities for a long time. in this paper, we propose a novel secure data aggregation scheme to simultaneously achieve privacy preservation and data integrity with differential privacy and fault tolerance. specifically, by introducing some auxiliary ciphertext subtly, a novel.

Electronics Free Full Text Data Integrity Preservation Schemes In In this chapter, we will introduce a novel secure data aggregation scheme to achieve privacy preservation and data integrity with differential privacy and fault tolerance (bao and lu, peer to peer. To design an efficient and secure data aggregation scheme fitting real applications has been pursued by research communities for a long time. in this paper, we propose a novel secure data aggregation scheme to simultaneously achieve privacy preservation and data integrity with differential privacy and fault tolerance. specifically, by introducing some auxiliary ciphertext subtly, a novel.

Comments are closed.