Five Key Measures To Prevent Cyber Attacks
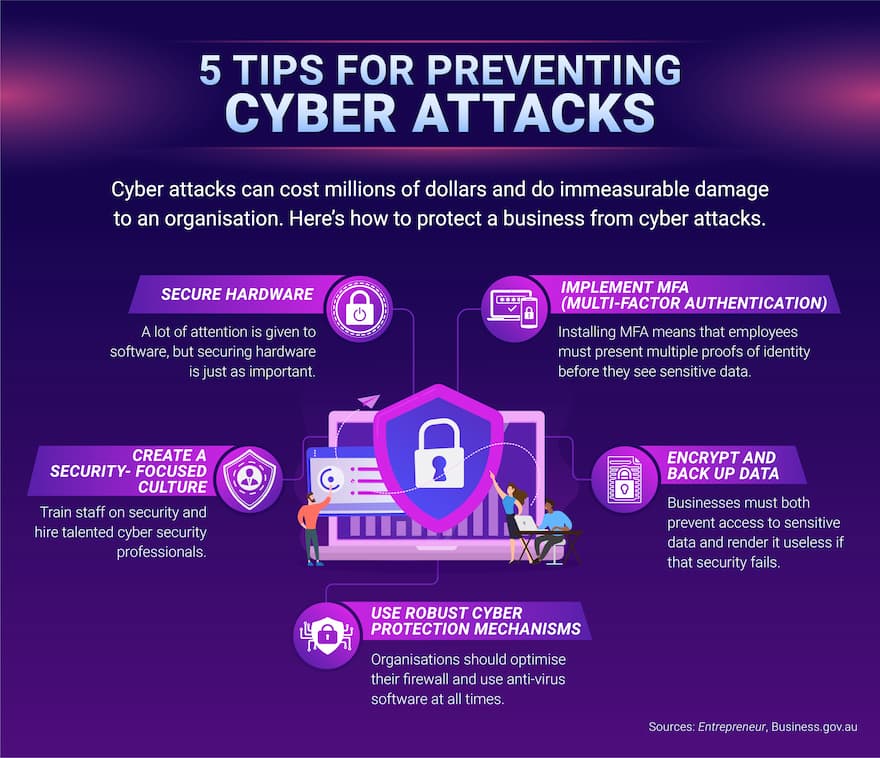
Cyber Attacks Tips For Protecting Your Organisation Ecu Online A firewall system will block any brute force attacks made on your network and or systems before it can do any damage, something we can help you with. 5. backup your data. in the event of a disaster (often a cyber attack) you must have your data backed up to avoid serious downtime, loss of data and serious financial loss. Cisa offers a range of cybersecurity services and resources focused on operational resilience, cybersecurity practices, organizational management of external dependencies, and other key elements of a robust and resilient cyber framework. cisa helps individuals and organizations communicate current cyber trends and attacks, manage cyber risks.
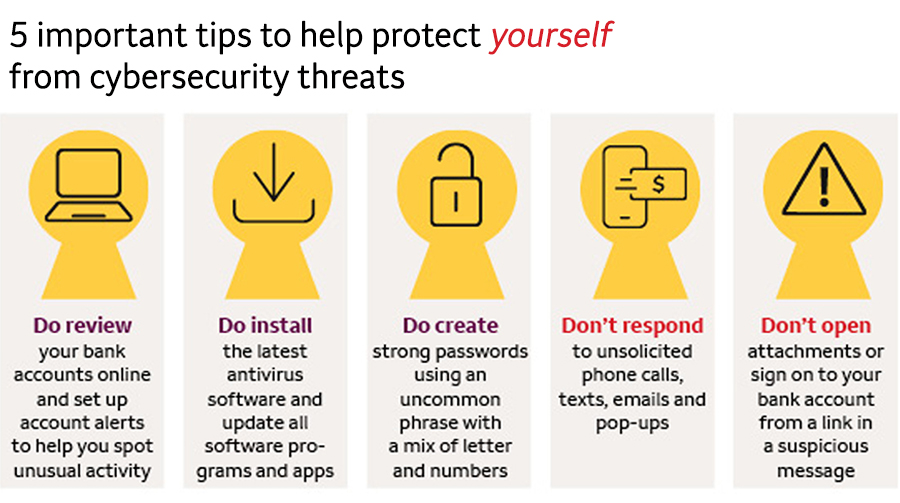
Tips For Safeguarding Against Cyberthreats Wells Fargo Stories Tips A cyber attack is an attempt by cybercriminals to disable computers, steal data, or use a breached computer system to launch additional attacks. cyber attacks have become more sophisticated in recent years and, as a result, cyber attack prevention is essential for every individual and organization. cybercrime is based upon the effective. Here are 10 practical strategies that you should implement. 1. encrypt your data and create backups. make sure all your sensitive data is encrypted. saving your data in normal text format only makes it easy for hackers to access. data encryption, on the other hand, limits data access to parties that have the encryption key. 4. backdoor trojan. backdoor trojan attacks involve malicious programs that can deceptively install malware or data and open up what’s referred to as the “backdoor” to your computer system. when attackers gain access to the backdoor, they can hijack the device without it being known to the user. 5. Prevention is the key to reducing the risk of a data breach. by investing in cybersecurity software, using a vpn, and being aware of common attack methods, individuals and organizations can deter hackers and keep their data private. sources . check point, “top 10 critical infrastructure and scada ics cybersecurity vulnerabilities and threats”.
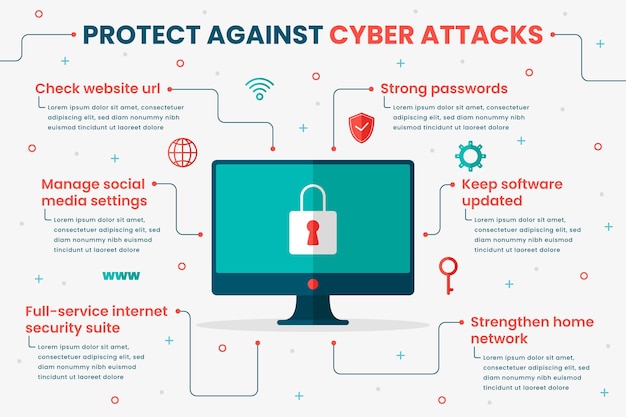
Protect Against Cyber Attacks Infographic Free Vector 4. backdoor trojan. backdoor trojan attacks involve malicious programs that can deceptively install malware or data and open up what’s referred to as the “backdoor” to your computer system. when attackers gain access to the backdoor, they can hijack the device without it being known to the user. 5. Prevention is the key to reducing the risk of a data breach. by investing in cybersecurity software, using a vpn, and being aware of common attack methods, individuals and organizations can deter hackers and keep their data private. sources . check point, “top 10 critical infrastructure and scada ics cybersecurity vulnerabilities and threats”. Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing. 3: keep software up to date. hackers often exploit vulnerabilities in outdated software to gain access to a system. therefore, it's essential to keep software up to date by applying patches and updates regularly. this includes not only operating systems but also software applications, plugins, and other components.

Cybersecurity Threats And Attacks All You Need To Know Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing. 3: keep software up to date. hackers often exploit vulnerabilities in outdated software to gain access to a system. therefore, it's essential to keep software up to date by applying patches and updates regularly. this includes not only operating systems but also software applications, plugins, and other components.

Ppt Measures To Avoid Cyber Attacks Powerpoint Presentation Free

Comments are closed.