Hacking Protect Yourself From Hackers The Dr Binocs Show о

Hacking Protect Yourself From Hackers The Dr Binocs Show P What is hacking? | hacking explained | who are hackers? | protect yourself from hackers | hacking passwords | how to protect your phone from getting hacked?. Hey kids, in this video, dr binocs will explain what is hacking? | the dr binocs show | peekaboo kidz. make sure you watch the whole video to know all the answers to your curious questions! show less.

Prime Video The Dr Binocs Show Hacking | protect yourself from hackers | the dr binocs show | peekaboo kidz why do paper cuts hurt so much? | how does your brain respond to pain? | the dr . What is a computer virus? | computer virus explained | types of computer virus | cybersecurity | computer security | protect yourself from hackers | malware. Hey kids, in this video, dr binocs will explain, "what is the ozone layer? why is there a hole in ozone layer? ozone layer depletion“ make sure you watch the whole video to know all the answers to your curious questions about our environment and earth’s ozone layer!. Hackers can use hacking to their advantage by leveraging their technical skills to exploit flaws in cybersecurity defenses. this may include gaining unauthorized access to networks, phones, computers, iot devices, software, and more. they can do this by exploiting either technical or social weaknesses.
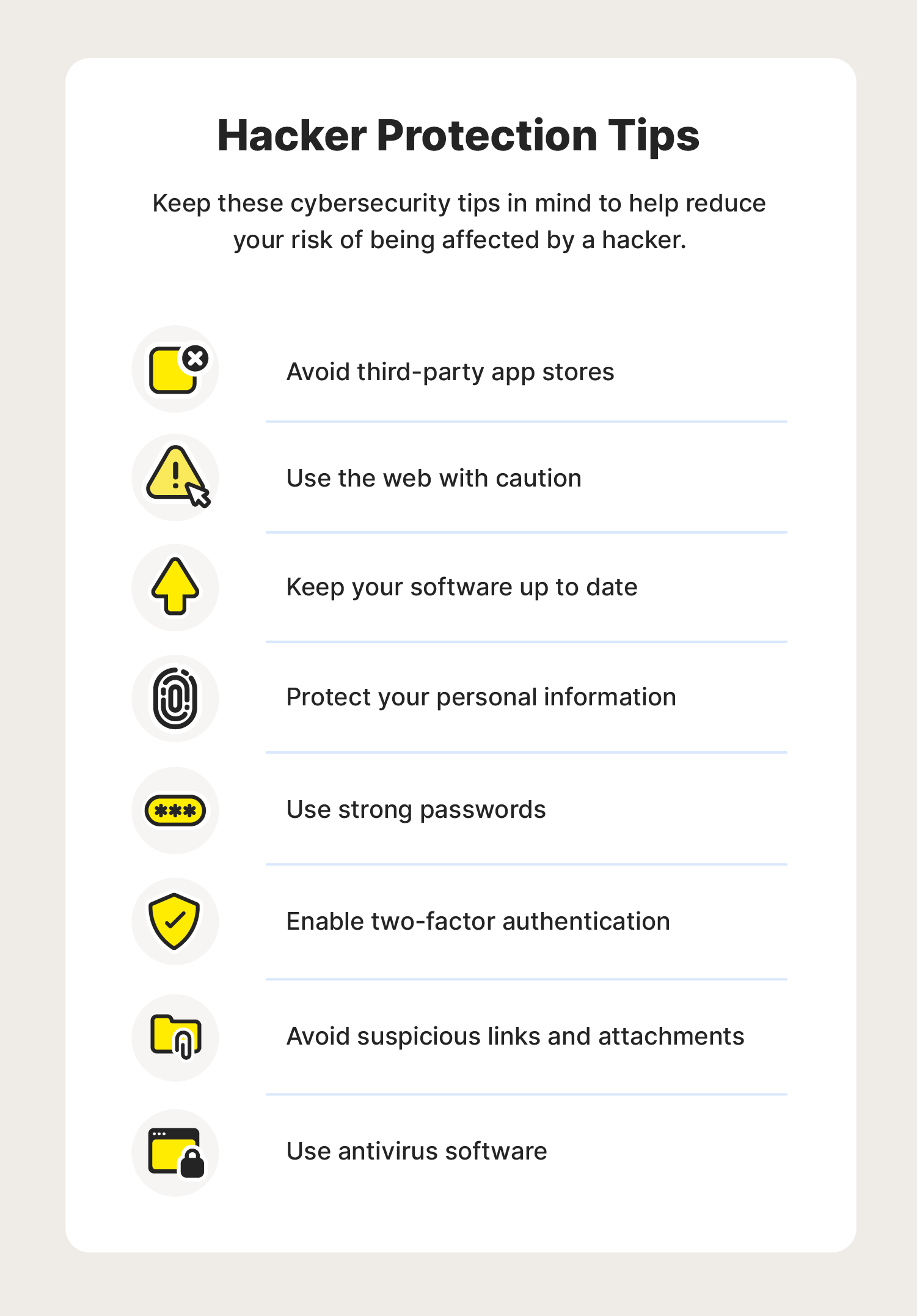
What Is A Hacker How To Protect Yourself Norton Hey kids, in this video, dr binocs will explain, "what is the ozone layer? why is there a hole in ozone layer? ozone layer depletion“ make sure you watch the whole video to know all the answers to your curious questions about our environment and earth’s ozone layer!. Hackers can use hacking to their advantage by leveraging their technical skills to exploit flaws in cybersecurity defenses. this may include gaining unauthorized access to networks, phones, computers, iot devices, software, and more. they can do this by exploiting either technical or social weaknesses. Click utilities, click firmware password utility, click turn on firmware password, and create your password. windows restart your computer, then hold down the bios key (typically esc, f1, f2, f8, f10, or del) as your computer boots up. use the arrow keys to select the password option, then enter your preferred password. 7. What is router hacking and how to prevent it. hacking isn’t just for computers — wi fi routers and cable modems can get hacked, too. and hackers use a wide range of techniques and tricks to access your data or place malware on your devices. learn how to protect yourself with our expert guides.
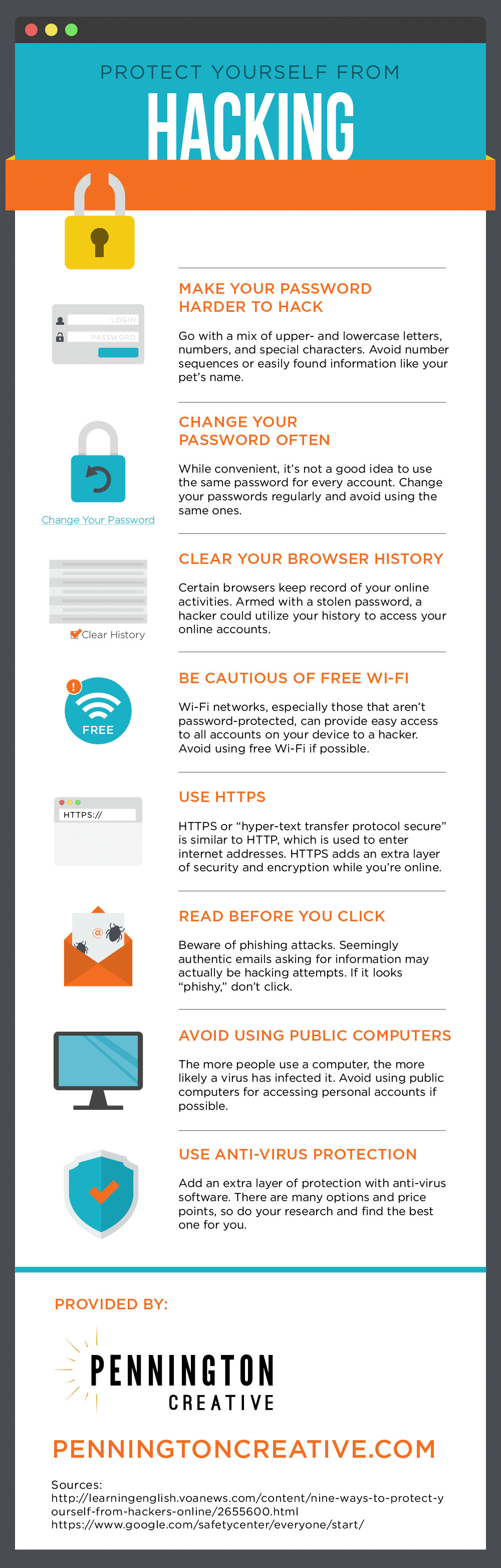
Protect Yourself From Hacking Pennington Creative Click utilities, click firmware password utility, click turn on firmware password, and create your password. windows restart your computer, then hold down the bios key (typically esc, f1, f2, f8, f10, or del) as your computer boots up. use the arrow keys to select the password option, then enter your preferred password. 7. What is router hacking and how to prevent it. hacking isn’t just for computers — wi fi routers and cable modems can get hacked, too. and hackers use a wide range of techniques and tricks to access your data or place malware on your devices. learn how to protect yourself with our expert guides.

Comments are closed.