History Of Cyber Kill Chain Steps Of Cyber Kill Chain Pros And Cons Of Cyber Kill Chain
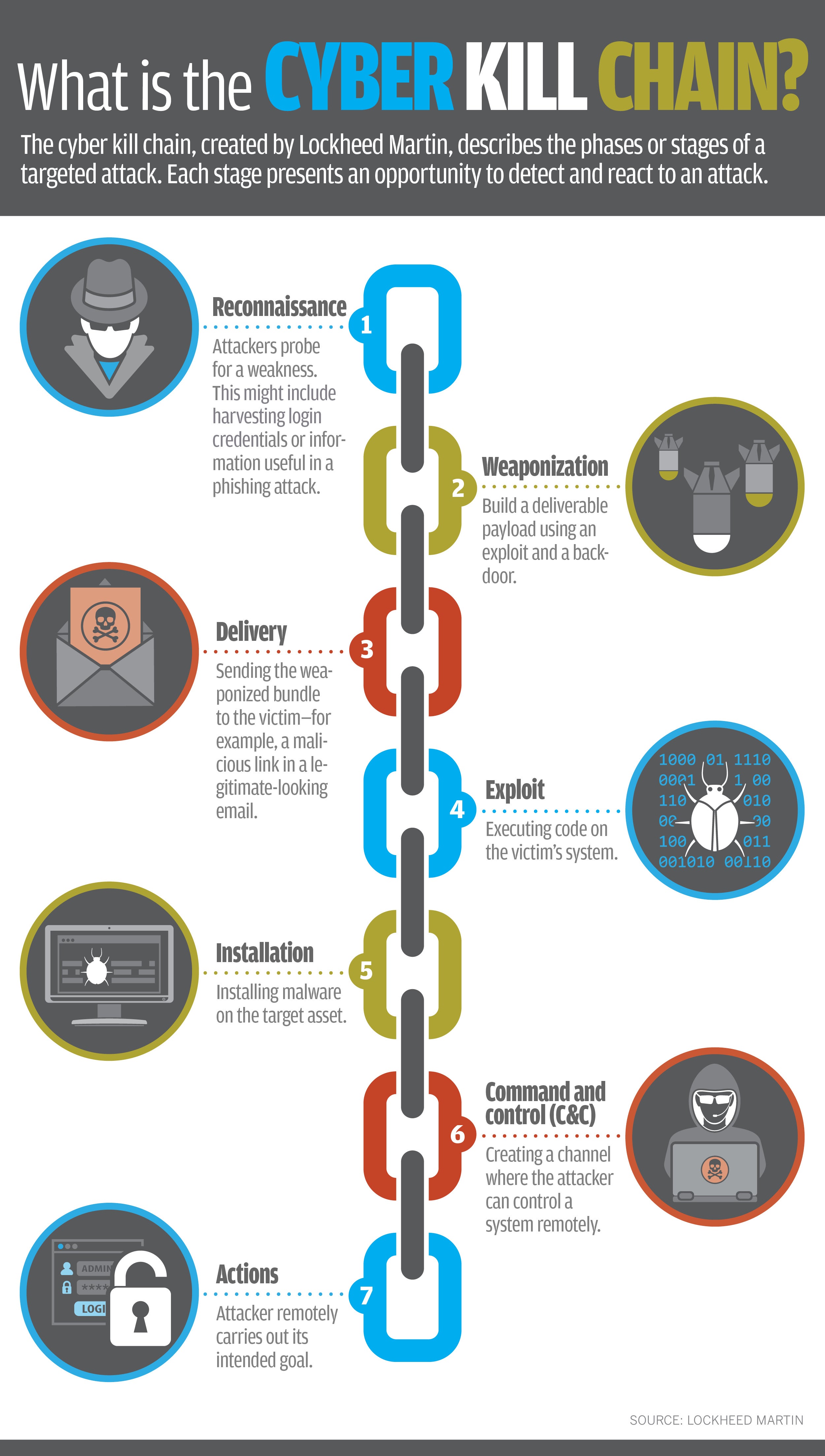
What Is The Cyber Kill Chain Why It S Not Always The Right Approach To The cyber kill chain is an adaptation of the military’s kill chain, which is a step by step approach that identifies and stops enemy activity. originally developed by lockheed martin in 2011, the cyber kill chain outlines the various stages of several common cyberattacks and, by extension, the points at which the information security team can. If you’re responsible for defending a network, this model can help you understand the stages of a cyberattack and the measures you can take to prevent or intercept each step. the cyber kill chain is divided into seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control (c2), and actions on objectives.
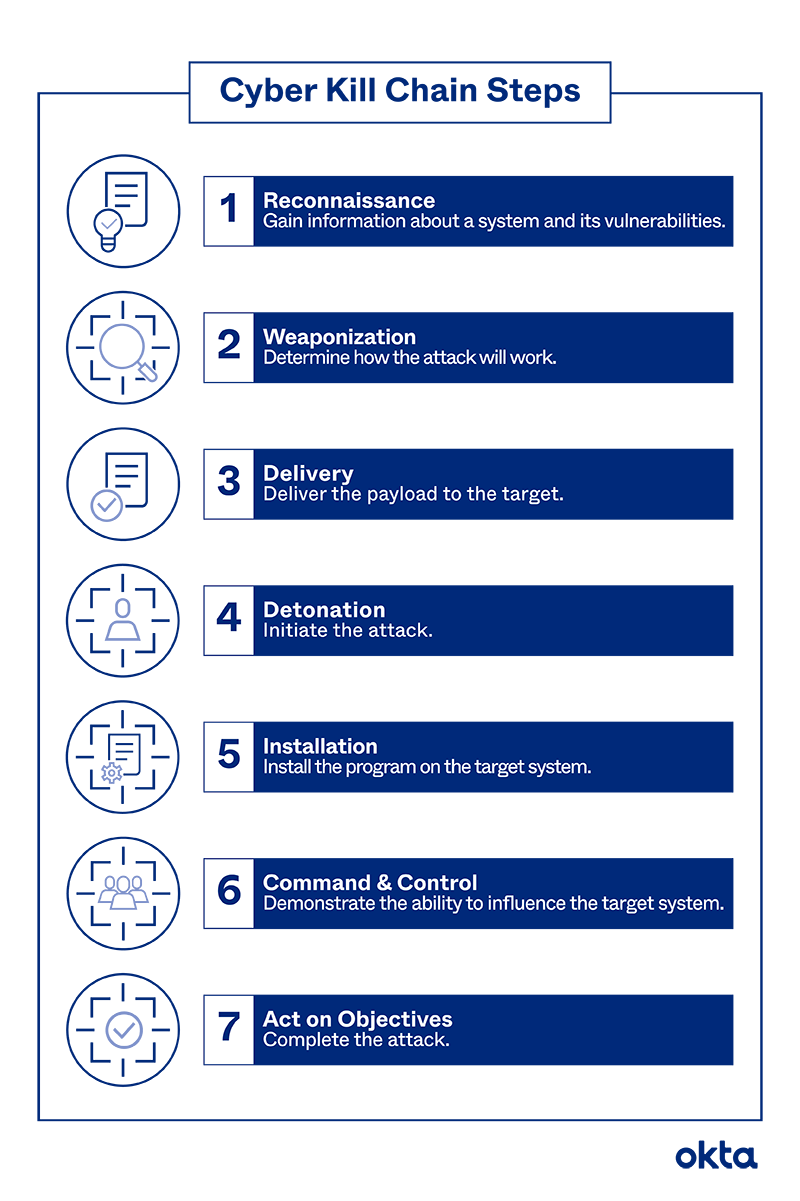
Cyber Kill Chain Definition And Steps Okta Cyber kill chain definition. the cyber kill chain, also known as the cyberattack lifecycle, is a model developed by lockheed martin that describes the phases of a targeted cyberattack. it breaks. Cyber kill chain definition. the cyber kill chain is a cyberattack deconstruction method that helps to understand the structure of an attack by tracing its stages from reconnaissance to information theft. lockheed martin developed this series of steps in 2011 using the military attack model, initially designed to identify and destroy a target. The original lockheed martin cyber kill chain model describes seven steps. this is the most commonly referenced framework in the industry. lockheed’s 7 stage cyber kill chain explores the methodology and motivation of a cybercriminal across the entire attack timeline, helping organizations to understand and combat threats. these seven phases are:. By sentinelone august 2, 2021. the cyber kill chain is a model that outlines the stages of a cyber attack. this guide explores each phase of the kill chain, from reconnaissance to execution, and how organizations can use this framework to enhance their security posture. learn about the importance of detection and response at each stage.
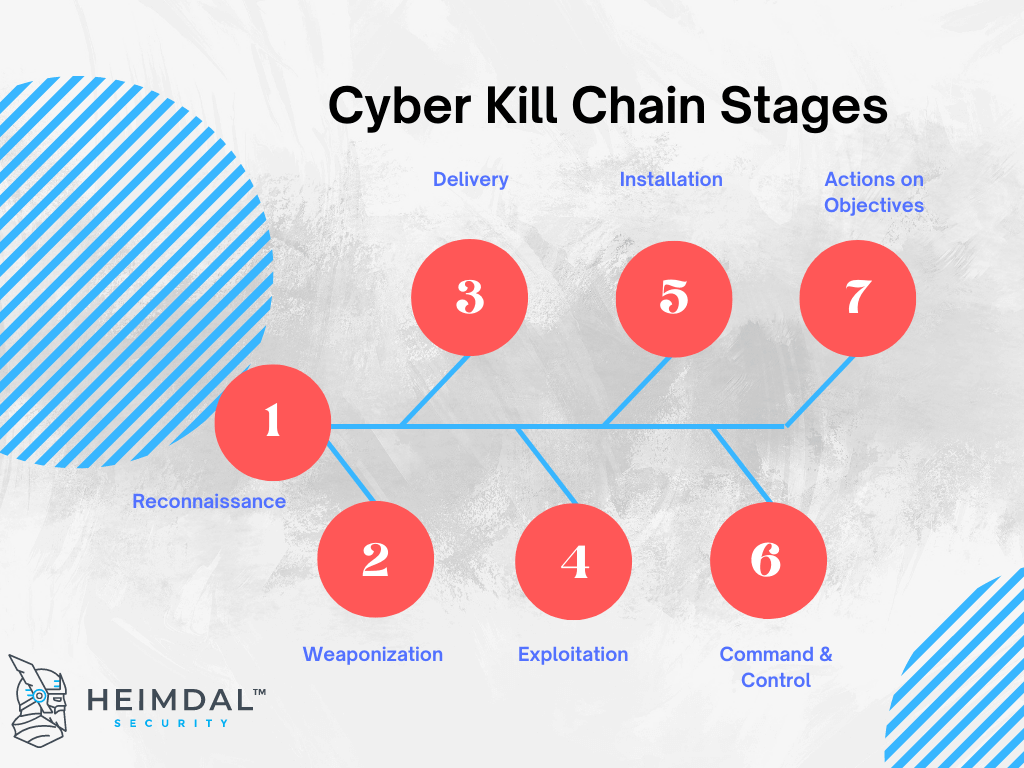
The Cyber Kill Chain Ckc Explained The original lockheed martin cyber kill chain model describes seven steps. this is the most commonly referenced framework in the industry. lockheed’s 7 stage cyber kill chain explores the methodology and motivation of a cybercriminal across the entire attack timeline, helping organizations to understand and combat threats. these seven phases are:. By sentinelone august 2, 2021. the cyber kill chain is a model that outlines the stages of a cyber attack. this guide explores each phase of the kill chain, from reconnaissance to execution, and how organizations can use this framework to enhance their security posture. learn about the importance of detection and response at each stage. The cyber kill chain is a cybersecurity model used to describe and track the stages of a cyberattack. fundamentally, the cybersecurity kill chain is the visualization and study of an attacker’s offensive behavior. this cybersecurity framework allows infosec teams to impede the assault during a certain stage and consequently design stronger. The cyber kill chain is the process by which perpetrators carry out cyberattacks. [2] lockheed martin adapted the concept of the kill chain from a military setting to information security, using it as a method for modeling intrusions on a computer network. [3] the cyber kill chain model has seen some adoption in the information security.

Cyber Kill Chain Model In Cyber Threat Intelligence Socradarв Cyber The cyber kill chain is a cybersecurity model used to describe and track the stages of a cyberattack. fundamentally, the cybersecurity kill chain is the visualization and study of an attacker’s offensive behavior. this cybersecurity framework allows infosec teams to impede the assault during a certain stage and consequently design stronger. The cyber kill chain is the process by which perpetrators carry out cyberattacks. [2] lockheed martin adapted the concept of the kill chain from a military setting to information security, using it as a method for modeling intrusions on a computer network. [3] the cyber kill chain model has seen some adoption in the information security.

Comments are closed.