How Hackers Are Hacking Your Phone Via Bluetooth
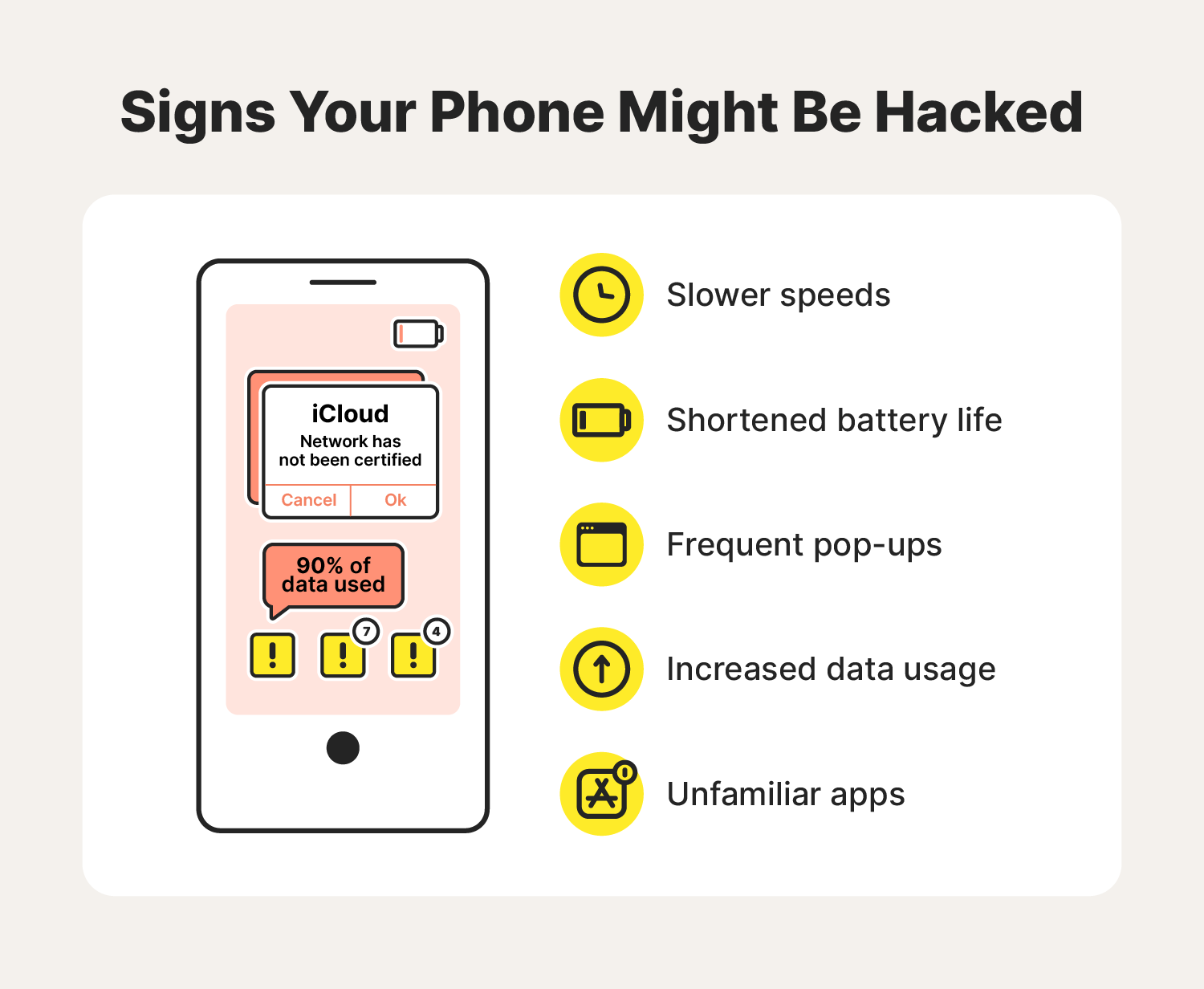
How To Remove A Hacker From My Phone Norton But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and You can also send a location tracking link to your spouse’s phone via any channel, from SMS to email or social media By clicking the link, they give their consent, and you can legally track

How To Hack Mobile Phone With Bluetooth Hacking Latest Software S 2015 More and more hackers are and also directly via browser Checking where you logged in with your WhatsApp account is simple Open the WhatsApp app on your mobile phone On iPhones and iPads Hackers are swiping passwords from Google accounts The attack locks you into your browser at the Google sign-in page and doesn’t allow you to leave, all while logging your email and password However, with these advancements come new challenges, namely, the risk of hacking some practical tips to help you keep your baby monitor safe from hackers so you can have peace of mind Likewise, there’s a lot hackers can do after malware is installed on your phone Keyloggers let them see everything you type on your phone, like account login information They might also be
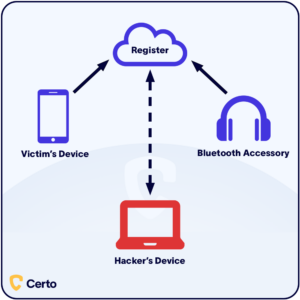
How To Tell If Your Bluetooth Is Hacked However, with these advancements come new challenges, namely, the risk of hacking some practical tips to help you keep your baby monitor safe from hackers so you can have peace of mind Likewise, there’s a lot hackers can do after malware is installed on your phone Keyloggers let them see everything you type on your phone, like account login information They might also be Learn more about iPhone malware and viruses We also have tips on how to protect your phone from hackers Roman is a Macworld Senior Editor with over 30 years of experience covering the tech We step you through everything you need to do to safeguard your data before you sell or trade in your current phone along with the best places to get cash or credit to put toward a new one Basically, they clone your key fob Once a thief gains access to a smart vehicle, they look for your car's on-board diagnostics board -- known as OBD board -- typically located below the steering More and more hackers are targeting regular people with you can do to protect yourself if you suspect someone got into your email or social media account A few years ago, I wrote a guide

How To Hack Smart Bluetooth Locks And Iot Devices вђ Check This Out Learn more about iPhone malware and viruses We also have tips on how to protect your phone from hackers Roman is a Macworld Senior Editor with over 30 years of experience covering the tech We step you through everything you need to do to safeguard your data before you sell or trade in your current phone along with the best places to get cash or credit to put toward a new one Basically, they clone your key fob Once a thief gains access to a smart vehicle, they look for your car's on-board diagnostics board -- known as OBD board -- typically located below the steering More and more hackers are targeting regular people with you can do to protect yourself if you suspect someone got into your email or social media account A few years ago, I wrote a guide

Comments are closed.