How To Encrypt And Decrypt Data In Python Using The R Vrogue Co
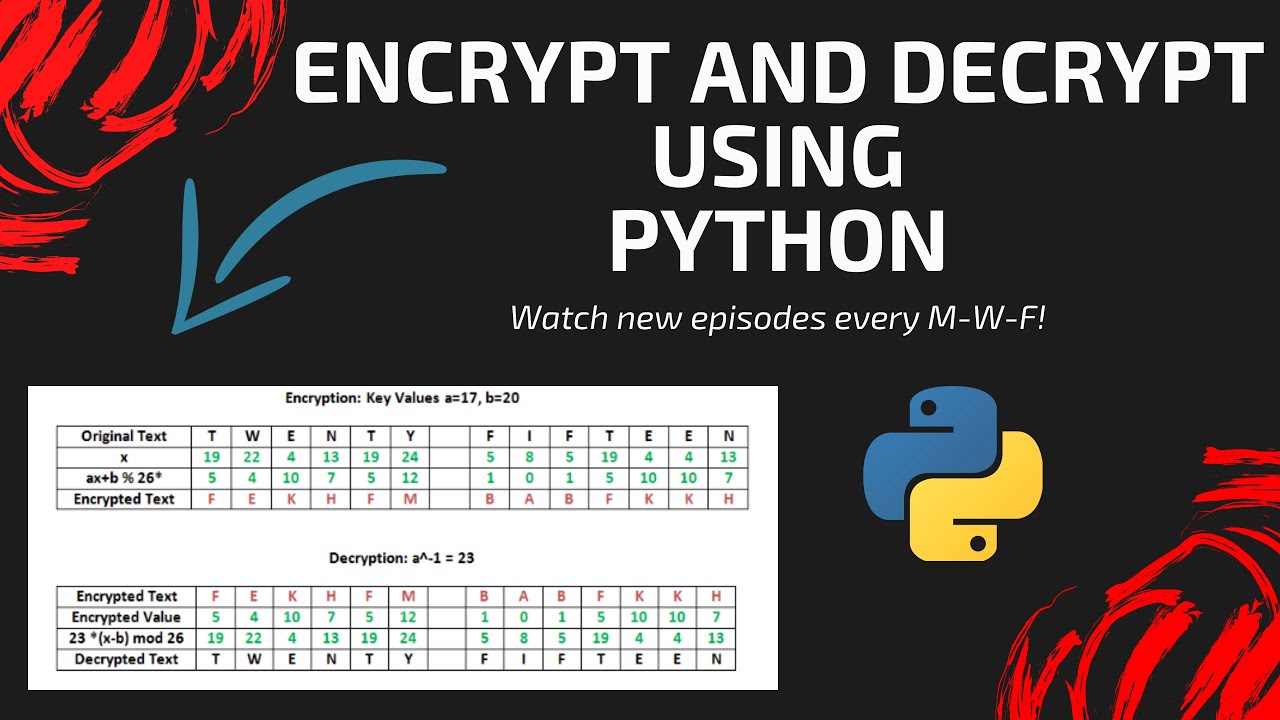
How To Encrypt And Decrypt Data In Python Using The R Vrogue Co Here's a simple and portable example that should be secure enough for basic string encryption needs. just put the pydes module in the same folder as your program and try it out: sender's computer. >>> from pydes import * # pydes if installed from pip. >>> ciphertext = triple des('a 16 or 24 byte password').encrypt("secret message", padmode=2) #. How asymmetric cryptography works by author rsa use cases. secure communication: tls ssl encryption for internet security.; digital signatures: verifies document authenticity through digital.
How To Encrypt And Decrypt Data Using Python Script Vrogue Co Now, we are ready to encrypt a message. this is a three step process: 1 encode the message. 2 initialize the fernet class. 3 pass the encoded message to encrypt() method. encode the message: message = "message i want to encrypt".encode() initialize the fernet class: f = fernet(key). The public exponent is used to encrypt messages, and in rsa commonly used numbers are 3, 17, or 65537 — and note these are prime numbers, that are co prime to the multiplied prime numbers making. Pycryptodome is a self contained python package of low level cryptographic primitives that supports python 2.6 and 2.7, python 3.4 and newer, and pypy. pycryptodome is a fork of pycrypto that has been enhanced to add more implementations and fixes to the original pycrypto library. where possible, most of the algorithms in this library are. Install the python rsa library with the following command. pip install rsa. steps: import rsa library. generate public and private keys with rsa.newkeys () method. encode the string to byte string. then encrypt the byte string with the public key. then the encrypted string can be decrypted with the private key.

Comments are closed.