Lockheed Martin Cyber Kill Chain вђ Illustrated Cybersec Nerds
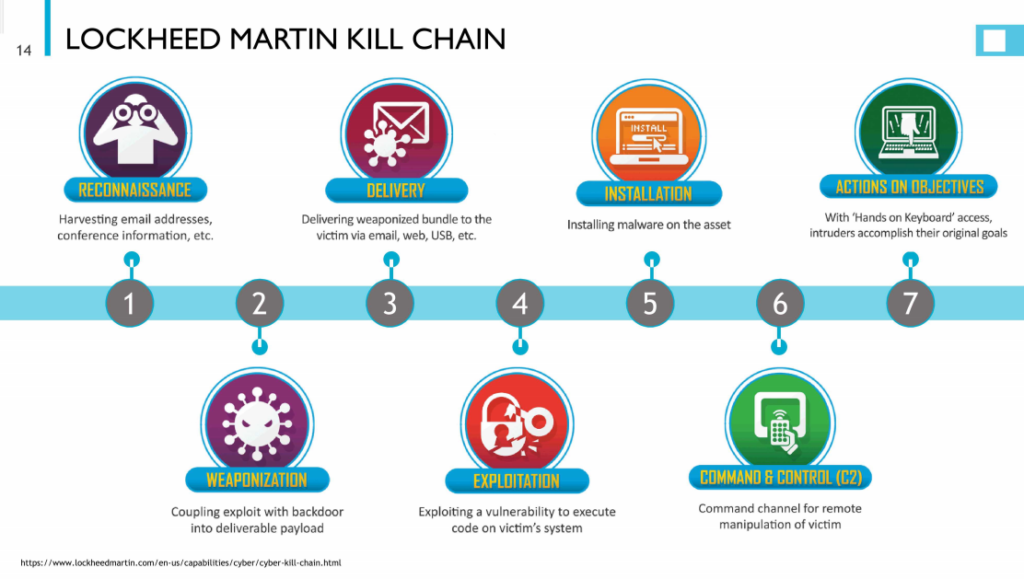
Lockheed Martin Cyber Kill Chain вђ Illustrated Cybersec о The cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data. the kill chain helps us understand and combat ransomware, security breaches, and advanced persistent attacks (apts). lockheed martin derived the kill chain framework from a military model – originally. Developed by lockheed martin, the cyber kill chain® framework is part of the intelligence driven defense® model for identification and prevention of cyber intrusions activity. the model identifies what the adversaries must complete in order to achieve their objective. the seven steps of the cyber kill chain® enhance visibility into an attack.
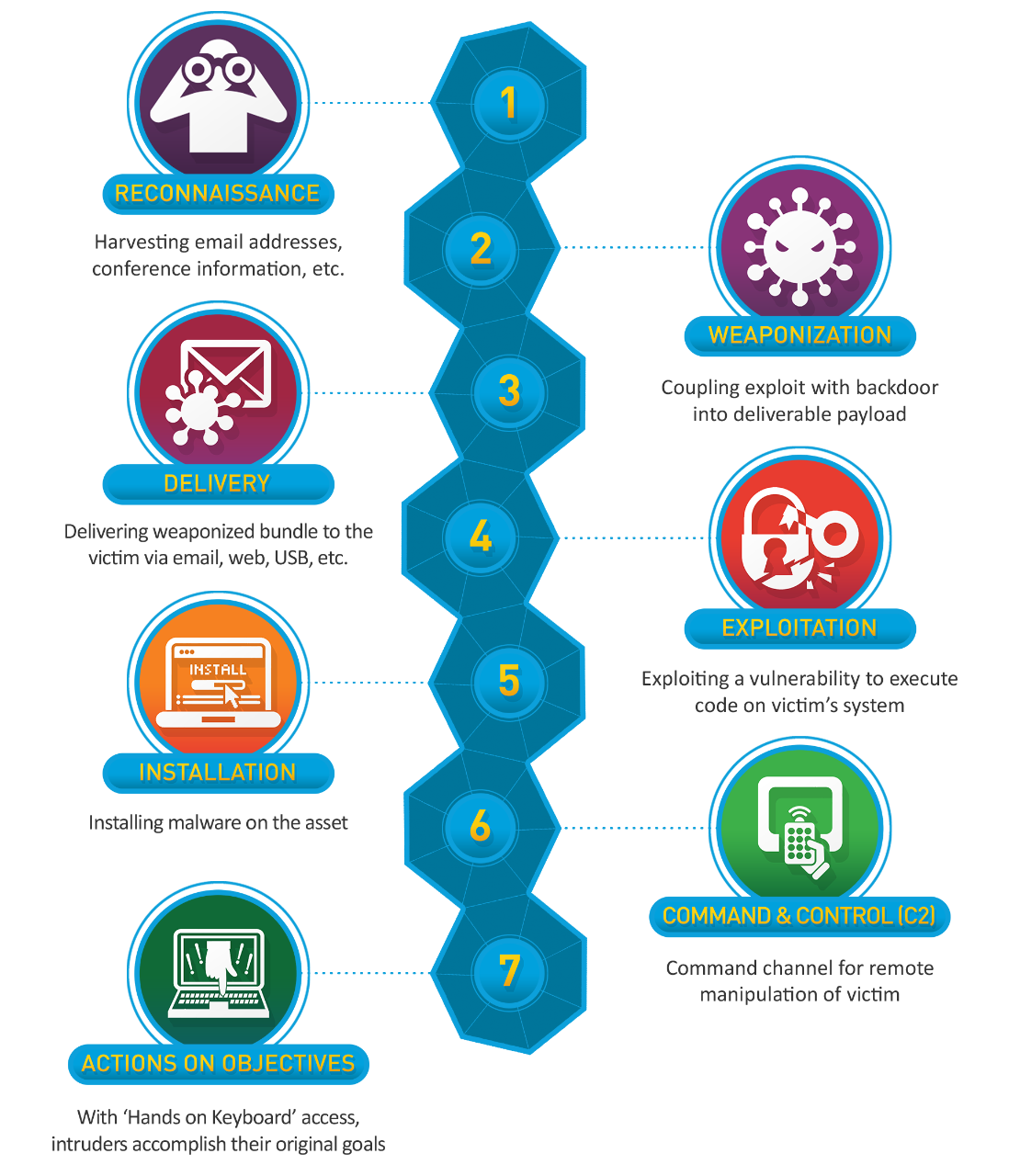
Cyber Kill Chainв Lockheed Martin Lockheed martin cyber kill chain — illustrated august 22, 2023 january 12, 2024 kiran dawadi 0 comments apt , attack , kill chain , lockheed martin ckc the cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the. Lockheed martin cyber kill chain — illustrated august 22, 2023 january 12, 2024 kiran dawadi 0 the cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the. The cyber kill chain framework, developed by lockheed martin (2022), explains how attackers move through networks to identify vulnerabilities that they can then exploit. attackers use the steps in the cyber kill chain when conducting offensive operations in cyberspace against their targets. The kill chain model is designed in seven steps: defender’s goal: understand the aggressor’s actions. ding is intelligenceintruder succeeds if, and only if, they can proceed through steps 1 6 and reach the final stage of t. identify the targetsthe adversaries are in the planning pha.
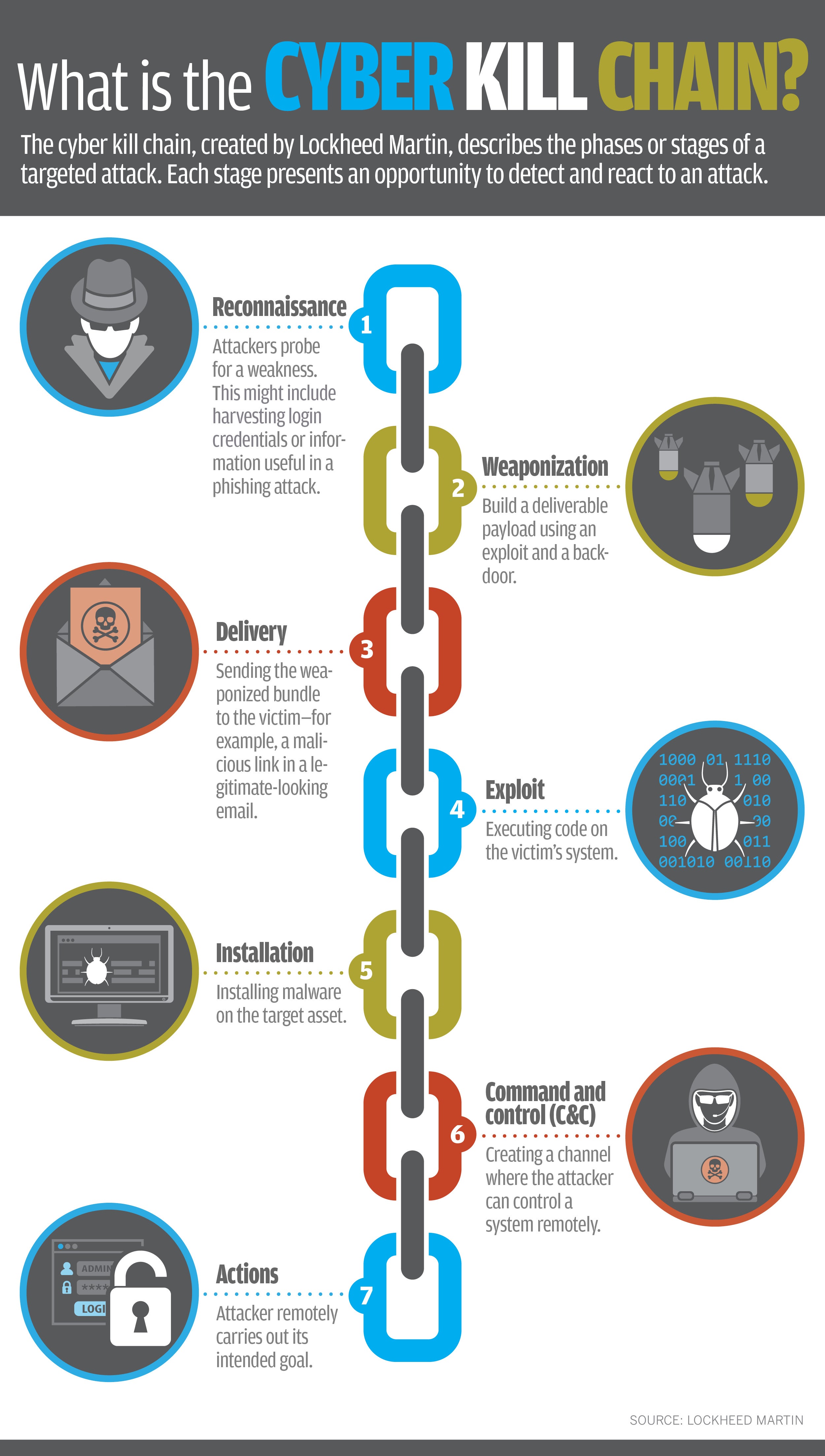
What Is The Cyber Kill Chain Why It S Not Always The Right Approach To The cyber kill chain framework, developed by lockheed martin (2022), explains how attackers move through networks to identify vulnerabilities that they can then exploit. attackers use the steps in the cyber kill chain when conducting offensive operations in cyberspace against their targets. The kill chain model is designed in seven steps: defender’s goal: understand the aggressor’s actions. ding is intelligenceintruder succeeds if, and only if, they can proceed through steps 1 6 and reach the final stage of t. identify the targetsthe adversaries are in the planning pha. The cyber kill chain is an adaptation of the military’s kill chain, which is a step by step approach that identifies and stops enemy activity. originally developed by lockheed martin in 2011, the cyber kill chain outlines the various stages of several common cyberattacks and, by extension, the points at which the information security team can. Cyber kill chain ® (ckc) or a similar practice and leverage the intelligence driven defense ® [1] (idd) approach to combat cyber threats. three primary gaps in this current state limit its effectiveness: 1. the behaviors, culture and the excessive amount of resources allocated to implementing and adhering to compliance requirements 2.

Lockheed Martin Cyber Kill Chain Explained Lockheed E Vrogue Co The cyber kill chain is an adaptation of the military’s kill chain, which is a step by step approach that identifies and stops enemy activity. originally developed by lockheed martin in 2011, the cyber kill chain outlines the various stages of several common cyberattacks and, by extension, the points at which the information security team can. Cyber kill chain ® (ckc) or a similar practice and leverage the intelligence driven defense ® [1] (idd) approach to combat cyber threats. three primary gaps in this current state limit its effectiveness: 1. the behaviors, culture and the excessive amount of resources allocated to implementing and adhering to compliance requirements 2.

Comments are closed.