Michael Parrella On Linkedin Secure File Sharing Digital Workplace

Michael Parrella On Linkedin Secure File Sharing Digital Workplace Don't miss eshare's transformative session, "project synergy: forging collaborative success between digital workplace and security," featuring: presenters: mike towers, founder & principal of. 💼 with our digital workplace services, you can expect: 🔹 seamless integration of cloud based tools and applications 🔹 enhanced communication and collaboration platforms 🔹 secure access.

Michael Parrella On Linkedin Redefining Secure Collaboration In The Secure file sharing is based on a document sharing tool or service managing the distribution of files across the network of devices. for example, such a file sharing platform can do the following: sync files. if your company has a byod policy, employees may use different devices to access work documents. a secure file sharing solution syncs. Dropbox. dropbox supports multiple file formats and offers share links and team folders. users can also work on dropbox projects offline, making this file sharing service travel friendly for digital nomads and other frequent flyers. dropbox’s slack integration allows for seamless sharing and collaboration right in slack. 1. address your company’s file sharing needs head on. a lot of file sharing happens at work. instead of ignoring data protection, make it a priority by finding a service that allows users to. Here’s what to look for when choosing and using a secure file sharing service based in the cloud: 1. use end to end encryption. make sure your files are end to end encrypted. with end to end encryption, you hold the encryption keys to your files, so only you and the people you share them with can access them. 2.
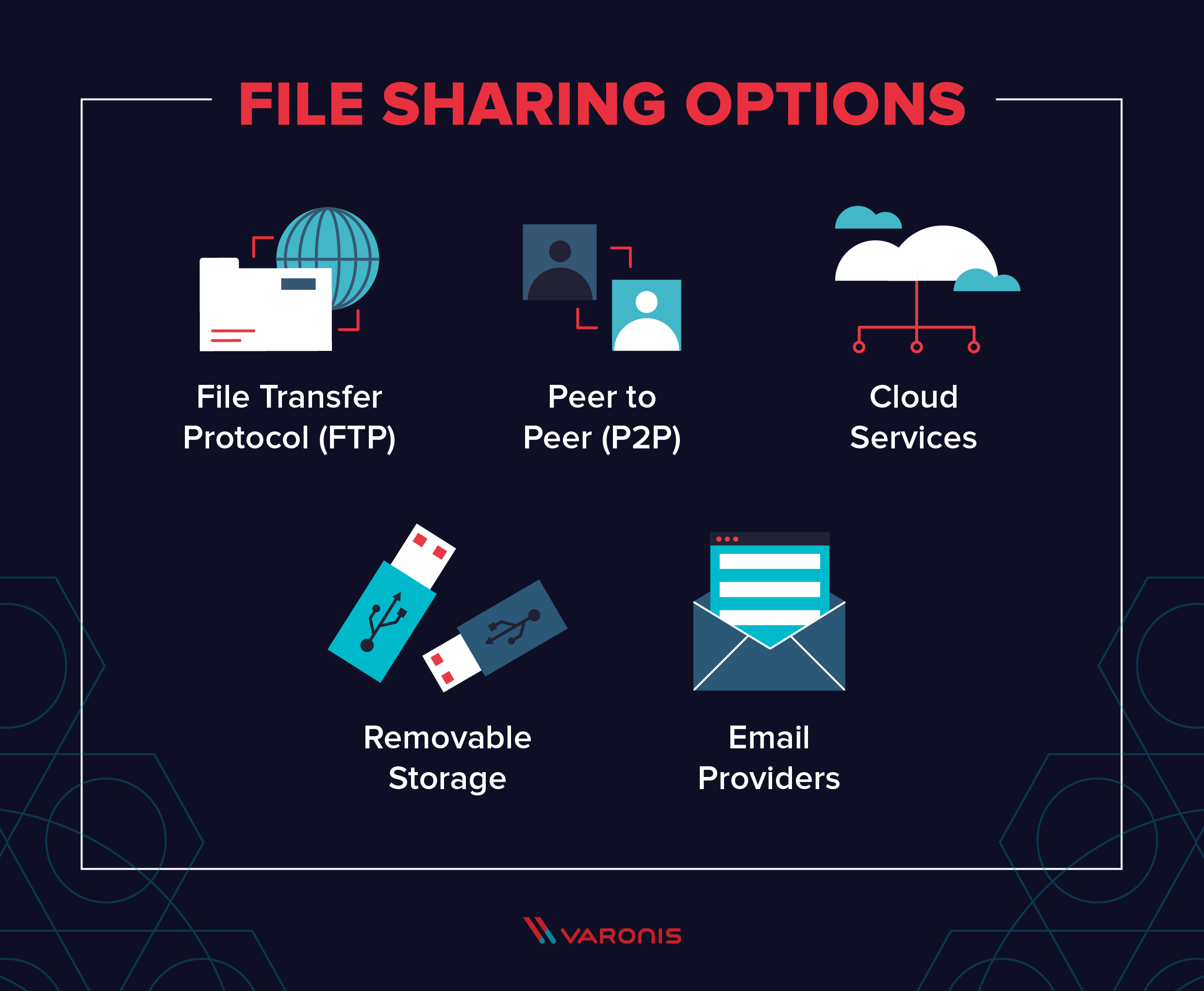
10 Secure File Sharing Options Tips And Solutions 1. address your company’s file sharing needs head on. a lot of file sharing happens at work. instead of ignoring data protection, make it a priority by finding a service that allows users to. Here’s what to look for when choosing and using a secure file sharing service based in the cloud: 1. use end to end encryption. make sure your files are end to end encrypted. with end to end encryption, you hold the encryption keys to your files, so only you and the people you share them with can access them. 2. Unauthenticated sharing: allowed: blocked: blocked: file sharing: allowed: allowed: limited to people in the team. team membership: anyone can join public teams. team owner approval required to join private teams. team owner approval required to join. team owner approval required to join. document encryption: available with sensitivity label. The first common practice is the use of sftp (ssh file transfer protocol) and is a reliable, tried and tested method to securely transfer files between different systems. it makes use of powerful algorithms like aes and triple des (among others) to secure and encrypt files. the second common method is use of a virtual private network (vpn.

Eshare On Linkedin Secure File Sharing Digital Workplace Modern Unauthenticated sharing: allowed: blocked: blocked: file sharing: allowed: allowed: limited to people in the team. team membership: anyone can join public teams. team owner approval required to join private teams. team owner approval required to join. team owner approval required to join. document encryption: available with sensitivity label. The first common practice is the use of sftp (ssh file transfer protocol) and is a reliable, tried and tested method to securely transfer files between different systems. it makes use of powerful algorithms like aes and triple des (among others) to secure and encrypt files. the second common method is use of a virtual private network (vpn.

Comments are closed.