The 7 Stages Of An Incident Response Plan

7 Phases Of Incident Response Essential Steps For A Comprehensive Jj provides insight into market trends, industry challenges, and solutions in the areas of incident response, endpoint security, risk management, and ransomware defense. most ir plans can be summed up in 4 common steps: preparation, detection & analysis, containment & eradication, and post incident activity. The 7 phases of incident response, as outlined by nist, are essential for organizations to build their own plans tailored to their specific needs. common pitfalls in planning should be avoided and outsourcing options considered when implementing an incident response plan. the importance of an incident response plan.
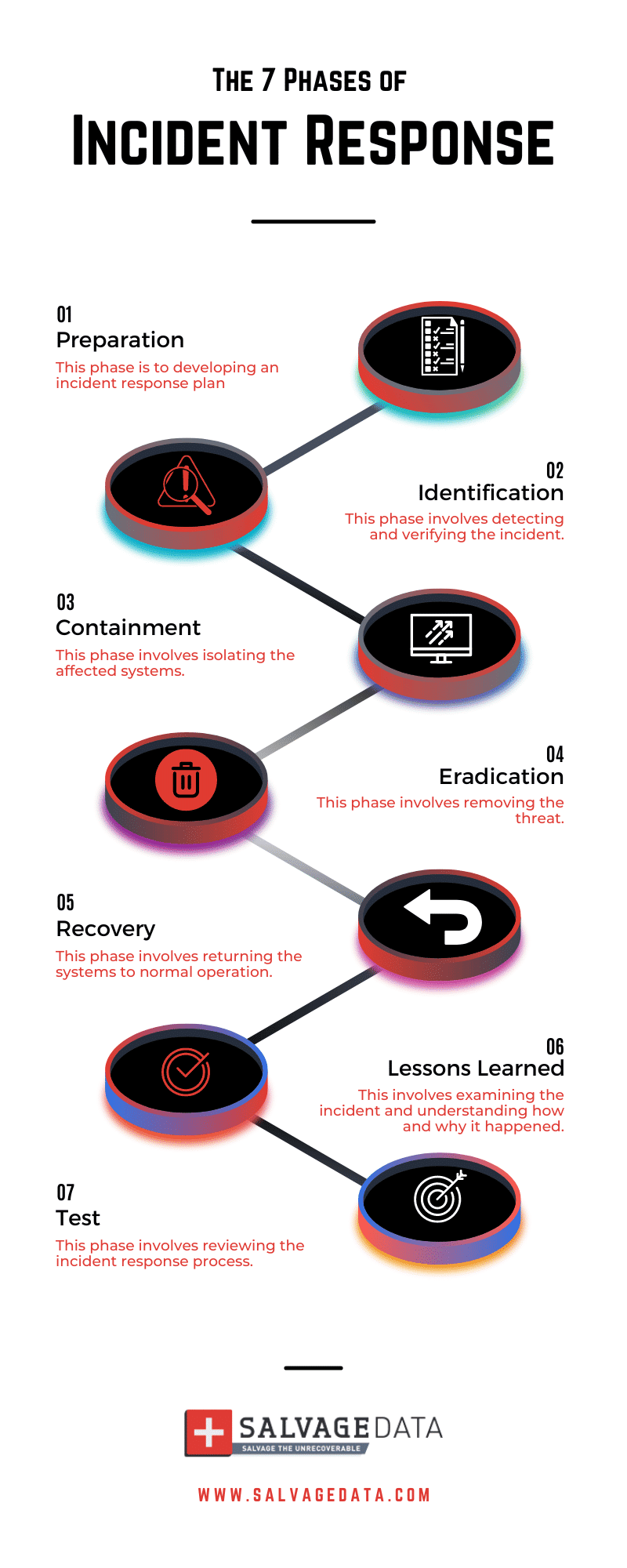
7 Phases Of An Incident Response How To Build An Ir Plan Salvagedata Preparation. threat detection. containment. investigation. eradication. recovery. follow up. partner with an expert managed security services provider (mssp) that can advise your team to best ensure your organization has defined and documented procedures and policies regarding the 7 phases of incident response. Stage 1: preparation. when in the middle of a cybersecurity incident, it's nearly impossible to create a well organized response to the threat at hand. thus, an incident response plan needs to be carefully prepared in advance. this will give your organization a fighting chance against the situation as it plays out in real time. The purpose is to collect data that will help prevent such situations in the future. 5. communication and reporting. effective communication is critical throughout the incident response process. However, many cybersecurity experts break this down into a more comprehensive or detailed list of 7 phases of incident response. so let’s take a look at what these 7 steps are: 1. preparation: as the name suggests, this phase of the incident response plan comes before the incident or data breach even takes place.
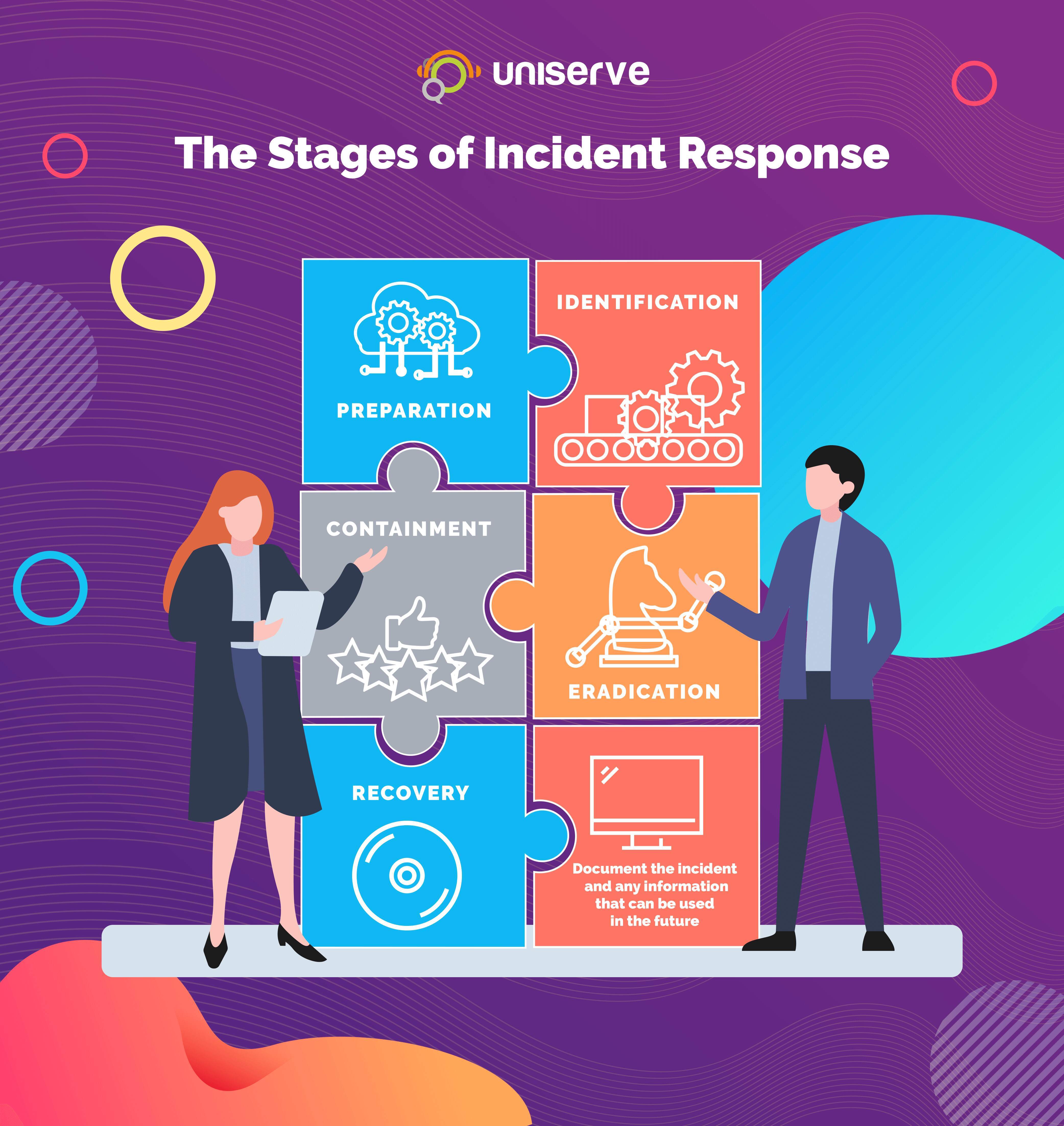
The Stages Of Incident Response Uniserve It Solutions The purpose is to collect data that will help prevent such situations in the future. 5. communication and reporting. effective communication is critical throughout the incident response process. However, many cybersecurity experts break this down into a more comprehensive or detailed list of 7 phases of incident response. so let’s take a look at what these 7 steps are: 1. preparation: as the name suggests, this phase of the incident response plan comes before the incident or data breach even takes place. Here is a step by step guide to the 7 steps of the incident response process. preparation. preparation for incident response involves developing a plan to effectively respond to and manage a security incident. this includes identifying potential risks, defining roles and responsibilities, establishing communication protocols, implementing. Incident response typically starts when the security team gets a credible alert from a security information and event management (siem) system. team members need to verify that the event qualifies as an incident and then isolate infected systems and remove the threat. if the incident is severe or takes a long time to resolve, organizations may.

Incident Response Plan The 7 Stages Techroots Here is a step by step guide to the 7 steps of the incident response process. preparation. preparation for incident response involves developing a plan to effectively respond to and manage a security incident. this includes identifying potential risks, defining roles and responsibilities, establishing communication protocols, implementing. Incident response typically starts when the security team gets a credible alert from a security information and event management (siem) system. team members need to verify that the event qualifies as an incident and then isolate infected systems and remove the threat. if the incident is severe or takes a long time to resolve, organizations may.

What Is Incident Response Plan Complete Guide

Comments are closed.