The Evolution Of Business Email Compromise Blog
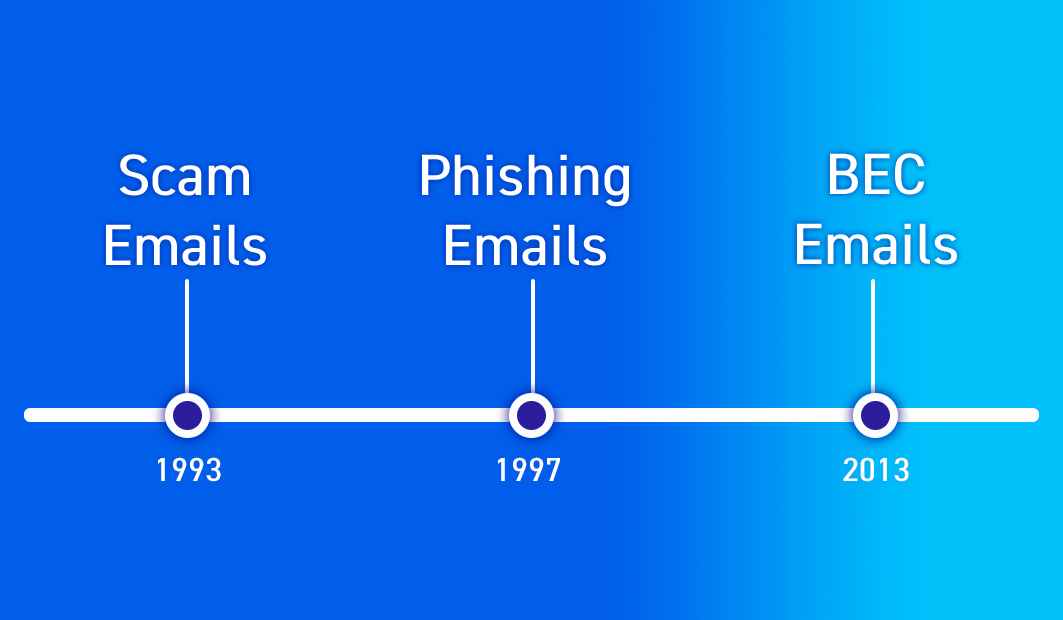
The Evolution Of Business Email Compromise According to the verizon 2022 data breach investigations report, most social engineering breaches happen through a business email compromise scam. but even though these attacks are identified as becs, they tend to be more complex than just some threat actor impersonating someone through a compromised email account. the report also reveals that:. Business email compromise is becoming increasingly common and the attacks are evolving into sophisticated and complex scams, making it more difficult for individuals and organizations to detect. according to the fbi's internet crime complaint center (ic3), bec attacks have resulted in losses totaling billions of dollars worldwide.

The Evolution Of Business Email Compromise Peerwise This blog is part three of a three part series focused on business email compromise. in the previous two blogs in this series, we detailed the evolution of business email compromise attacks and how microsoft defender for office 365 employs multiple native capabilities to help customers prevent these attacks. in part one, we covered some of the. These first instances of business email compromise (bec) kicked off a decade of attacks that use this simple yet highly effective scheme. while the threat has evolved, threat actors continue to. Microsoft 365 defender researchers recently uncovered and disrupted a large scale business email compromise (bec) infrastructure hosted in multiple web services. attackers used this cloud based infrastructure to compromise mailboxes via phishing and add forwarding rules, enabling these attackers to get access to emails about financial transactions. The term itself has seen an evolution over the years, but quite simply business email compromise (bec) is a type of phishing attack that targets organizations with a view to steal money or sensitive information. at its core, it’s a social engineering attack, where the attacker looks to dupe the target into believing that they are interacting.

Comments are closed.