Types Of Cyber Attacks Hacking Attacks And Techniques Dataflair
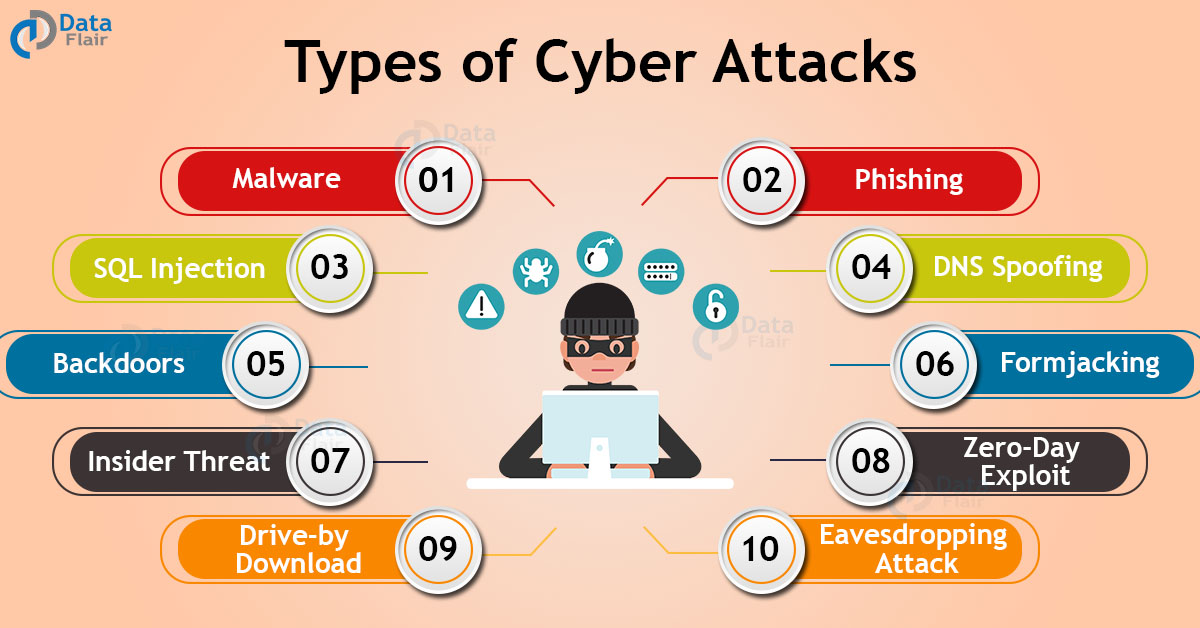
Types Of Cyber Attacks Hacking Attacks And Techniques Dataflair An attack in the system. these attacks target a particular node (computer in a network) and try to exploit it. the major types of cyberattacks are: malware. phishing. sql injection. man in the middle (mitm) attack. denial of service (dos) and distributed denial of service (ddos) dns spoofing. 1. recreational cyber attackers. the main motive behind these types of attackers is fame and notoriety. they have limited resources and know which vulnerability to exploit for their cause. 2. script kiddies cyber attackers. these are amateurs who learn from the internet and use available tools to crack a system.
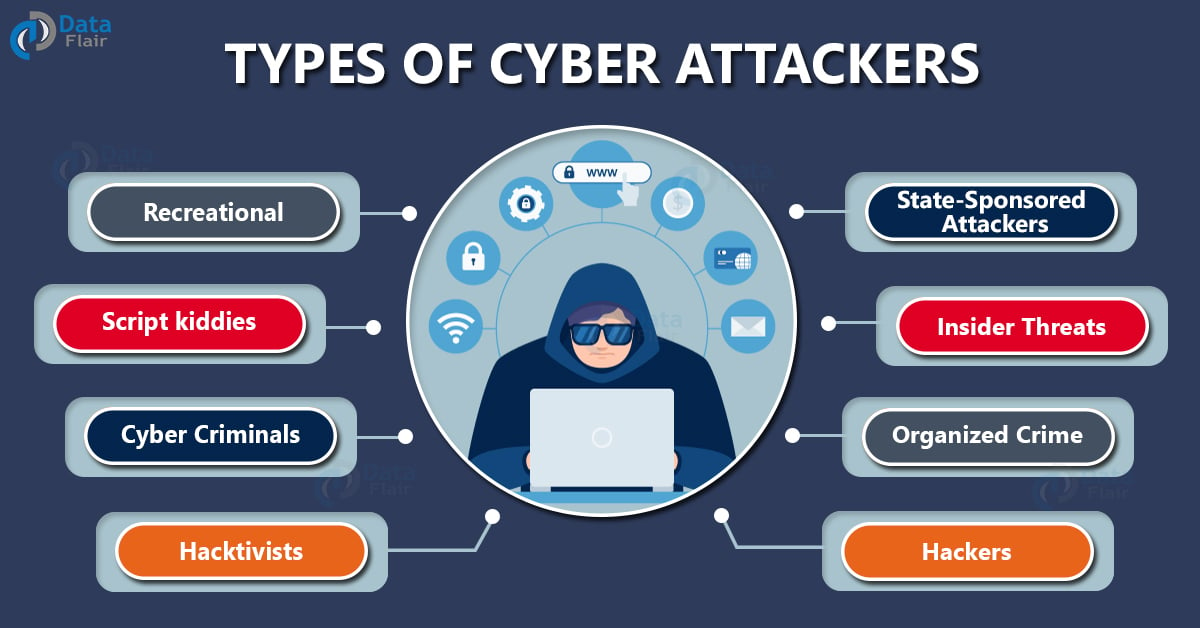
Most Common Types Of Cyber Attackers Dataflair A cyberattack – also known as a cybersecurity attack – is any form of malicious activity targeting it systems and or the attackers or threat actors using them to gain unauthorized access to systems and data they contain. criminals typically are looking to exploit an attack for financial gain, but in other cases the aim is to disrupt. 1. malware. malware — or malicious software — is any program or code that is created with the intent to do harm to a computer, network or server. malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any. 5. cryptojacking. cryptojacking refers to a hacker’s covert efforts to commandeer a computer’s processing power for the purpose of mining cryptocurrencies, like bitcoin and ether, while the user is unaware or non consenting. jeopardized systems suffer a slow processing speed. 6. 5. ransomware. ransomware is malicious software that cyberattackers can install on your device, allowing them to block your access until you pay the attackers a ransom. however, paying the ransom doesn’t guarantee the removal of the software, so experts often advise individuals not to pay the ransom if possible. 6.
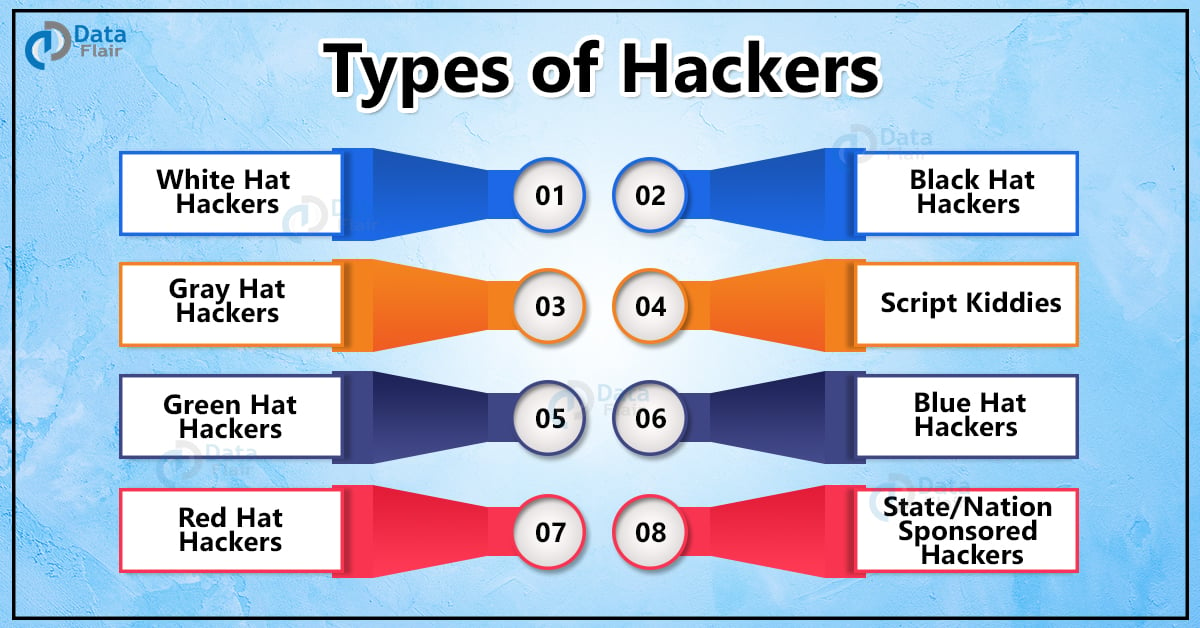
19 Types Of Hackers You Should Be Aware Of Dataflair 5. cryptojacking. cryptojacking refers to a hacker’s covert efforts to commandeer a computer’s processing power for the purpose of mining cryptocurrencies, like bitcoin and ether, while the user is unaware or non consenting. jeopardized systems suffer a slow processing speed. 6. 5. ransomware. ransomware is malicious software that cyberattackers can install on your device, allowing them to block your access until you pay the attackers a ransom. however, paying the ransom doesn’t guarantee the removal of the software, so experts often advise individuals not to pay the ransom if possible. 6. In fact, it has become a competitive advantage for some companies. this article describes the 12 most common cyber threats today and provides cyber attack examples. 1. denial of service (dos) and distributed denial of service (ddos) attacks. both denial of service and distributed denial of service attacks are malicious attempts to make a server. Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing.

14 Most Common Types Of Cyber Attacks And How To Prevent Them In fact, it has become a competitive advantage for some companies. this article describes the 12 most common cyber threats today and provides cyber attack examples. 1. denial of service (dos) and distributed denial of service (ddos) attacks. both denial of service and distributed denial of service attacks are malicious attempts to make a server. Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing.
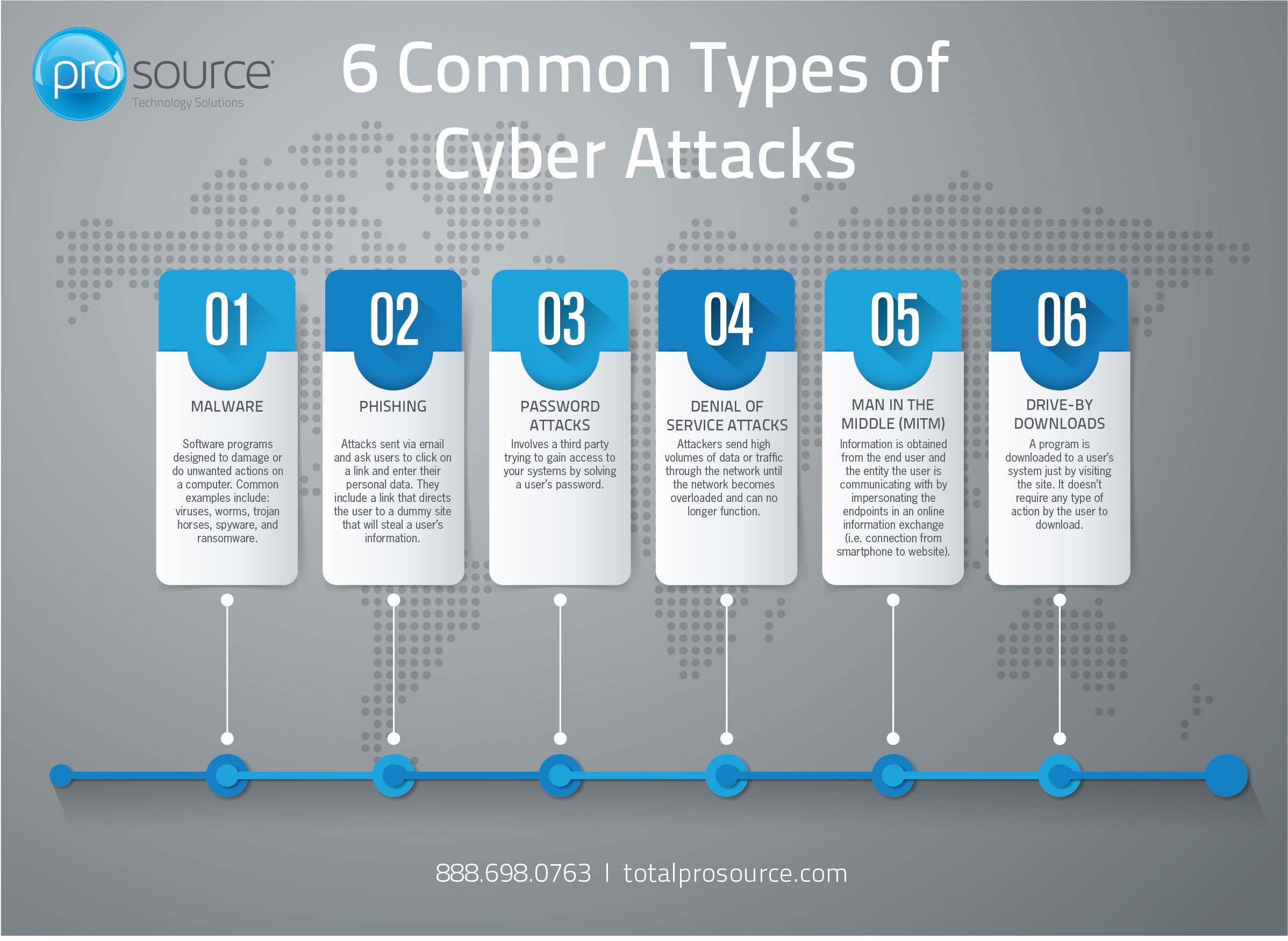
6 Common Types Of Cyber Attacks

Comments are closed.