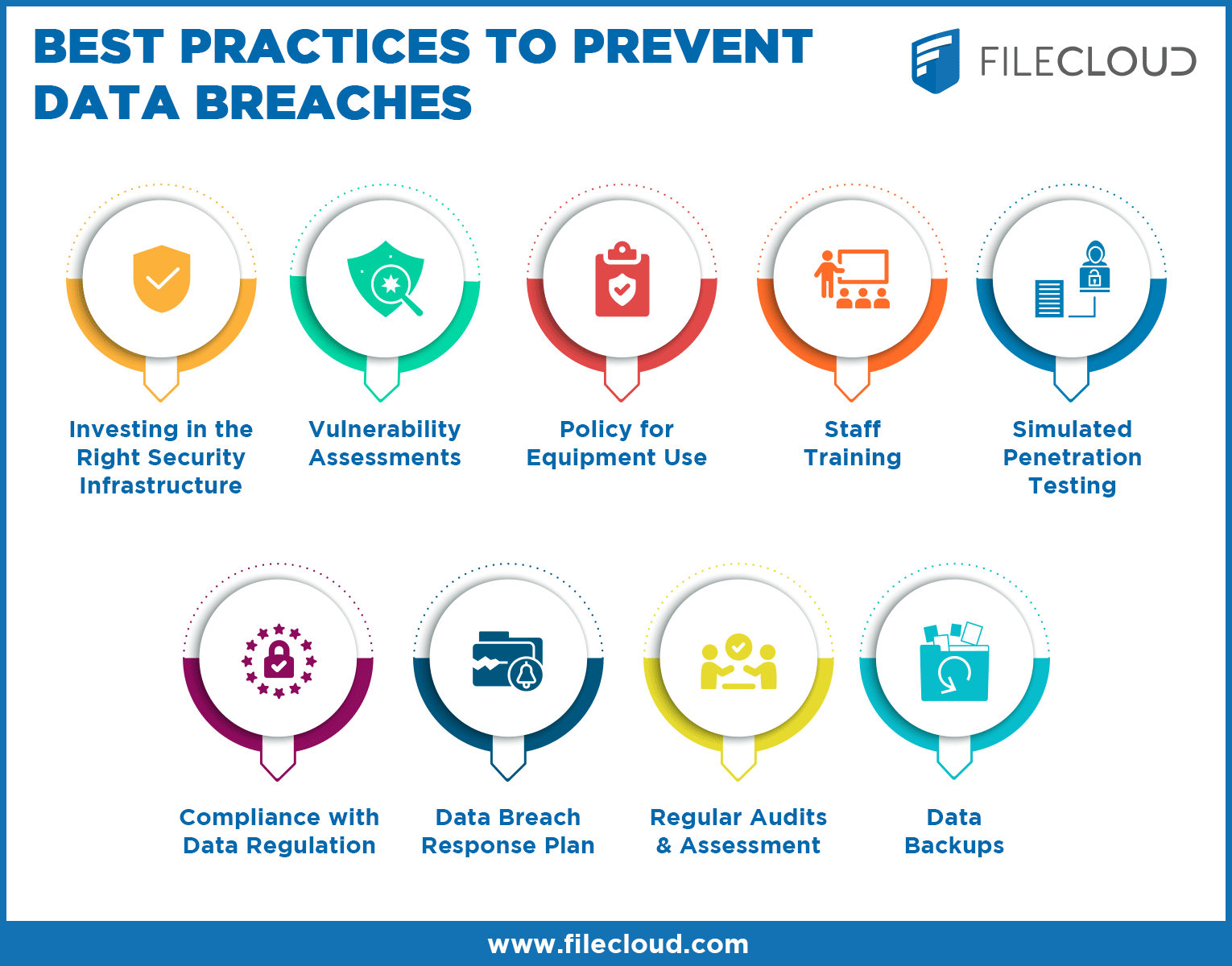
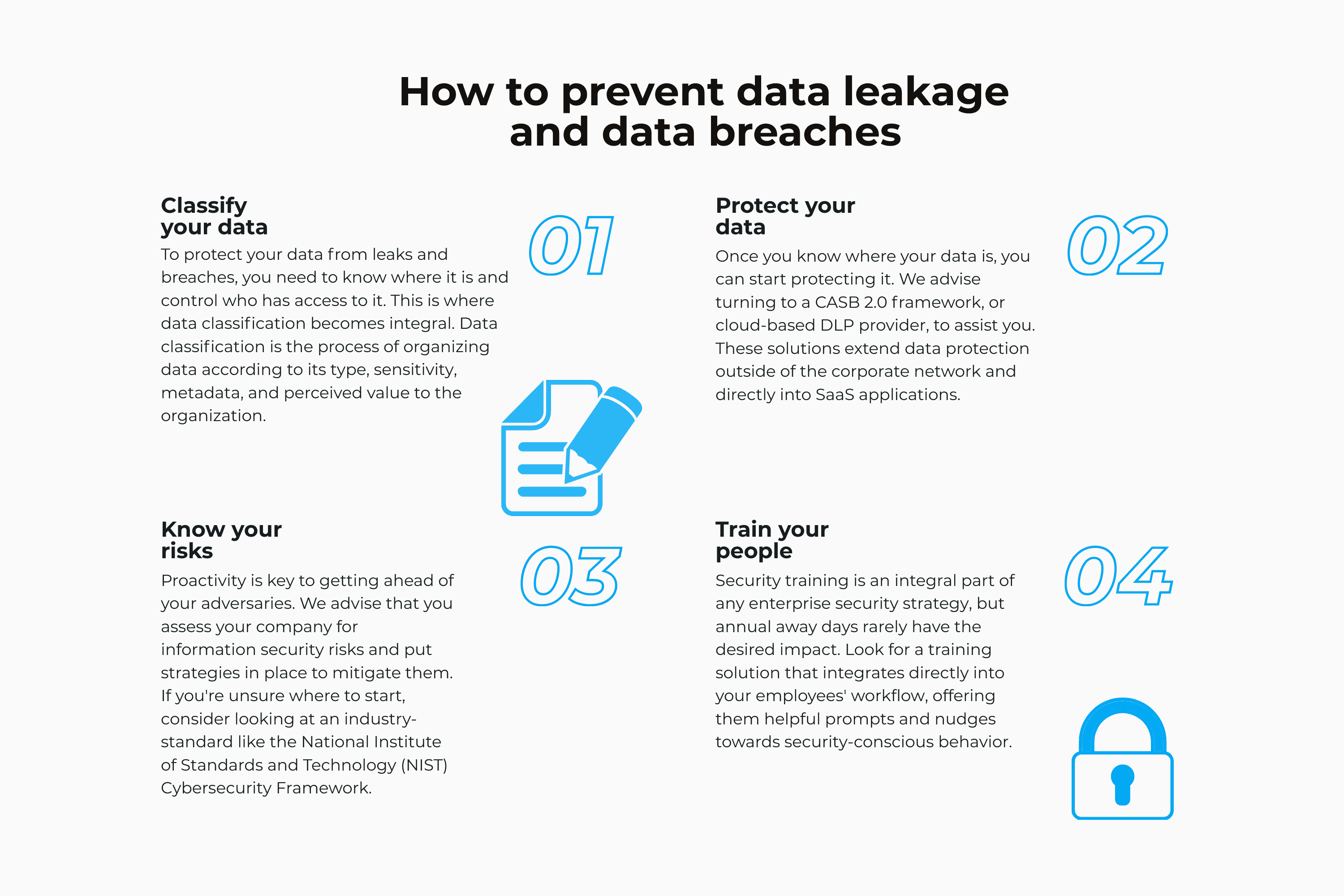
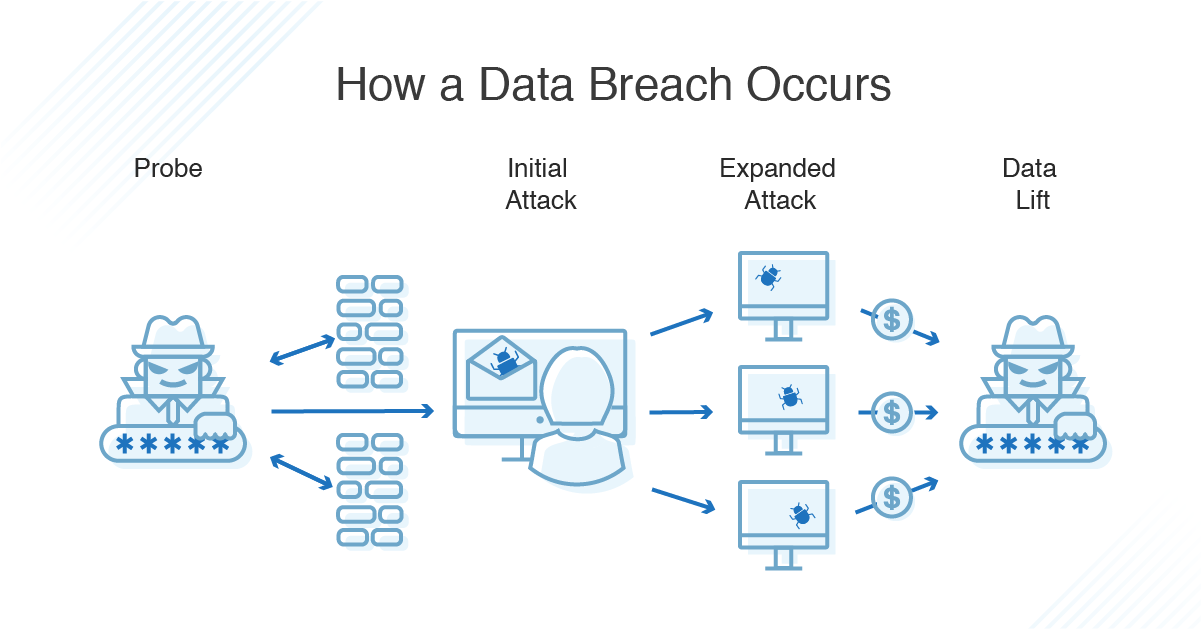
What Is A Data Breach How To Prevent Data Leaks
What Is Data Leakage Data Leak Prevention Tips Vrogue Co Check if your Social Security number was stolen in the massive data theft and what to do to secure your personal information The threat most users are aware of is the sale of fraudulent products Just because it’s advertised on social media doesn’t mean that it’s a reliable and trustworthy seller In fact, about 44% of
What Is The Difference Between A Data Breach Data Leak Polymer SIM-swapping is a growing form of identity theft that goes beyond hacking into an email or social media account In this case, the thieves take over your phone number Any calls or texts go to them, Thousands of records belonging to Confidant Health, an AI-powered service offering mental health and addiction treatment in the US, were exposed online according to cybersecurity researcher Jeremiah Security researchers say that thousands of companies are potentially leaking secrets from their internal knowledge base (KB) articles via ServiceNow misconfigurations You have antivirus, a VPN, and other security software on your PC, phone, and tablet, but how do you know if it's keeping you safe? Here are a dozen tips for performing your own security checkup
What Is A Data Breach Definition Types Dnsstuff Security researchers say that thousands of companies are potentially leaking secrets from their internal knowledge base (KB) articles via ServiceNow misconfigurations You have antivirus, a VPN, and other security software on your PC, phone, and tablet, but how do you know if it's keeping you safe? Here are a dozen tips for performing your own security checkup Cybersecurity giant Fortinet has confirmed it suffered a data breach after a threat actor extort Fortinet into paying a ransom, likely to prevent the publishing of data, but the company Explore how ATO attacks work, how to identify them and learn good online practices you can adopt to protect your data, identity, and finances In the first half of 2024 alone, India has witnessed 593 cyber incidents, comprising of 388 data breaches, 107 data leaks, and 39 ransomware attacks With an average of 3,201 cyberattacks per week in Fraudsters are using photos of your home in a newly uncovered “hello pervert” sextortion campaign—here’s how to protect yourself from this alarming threat

What Is A Data Breach And How To Prevent Data Leaks Vulners Cybersecurity giant Fortinet has confirmed it suffered a data breach after a threat actor extort Fortinet into paying a ransom, likely to prevent the publishing of data, but the company Explore how ATO attacks work, how to identify them and learn good online practices you can adopt to protect your data, identity, and finances In the first half of 2024 alone, India has witnessed 593 cyber incidents, comprising of 388 data breaches, 107 data leaks, and 39 ransomware attacks With an average of 3,201 cyberattacks per week in Fraudsters are using photos of your home in a newly uncovered “hello pervert” sextortion campaign—here’s how to protect yourself from this alarming threat 17 blog post by AppOmni researchers explained that this data can often be sensitive it’s up to organizations to prevent these leaks, said Meged This past May, Meged said the Adaptive

What Is A Data Breach How To Prevent Data Leaks In the first half of 2024 alone, India has witnessed 593 cyber incidents, comprising of 388 data breaches, 107 data leaks, and 39 ransomware attacks With an average of 3,201 cyberattacks per week in Fraudsters are using photos of your home in a newly uncovered “hello pervert” sextortion campaign—here’s how to protect yourself from this alarming threat 17 blog post by AppOmni researchers explained that this data can often be sensitive it’s up to organizations to prevent these leaks, said Meged This past May, Meged said the Adaptive

Comments are closed.