What Is Cyber Kill Chain вђ Cyphere

What Is Cyber Kill Chain вђ Cyphere Like the military’s kill chain, the cyber kill chain has seven crucial steps to manage, protect, and improve network systems. the steps are as follows: 1. reconnaissance. at this stage of the attack, the criminals gather as much info they can access about their targets. this is where the cyber attack starts. The cyber kill chain is an adaptation of the military’s kill chain, which is a step by step approach that identifies and stops enemy activity. originally developed by lockheed martin in 2011, the cyber kill chain outlines the various stages of several common cyberattacks and, by extension, the points at which the information security team can.
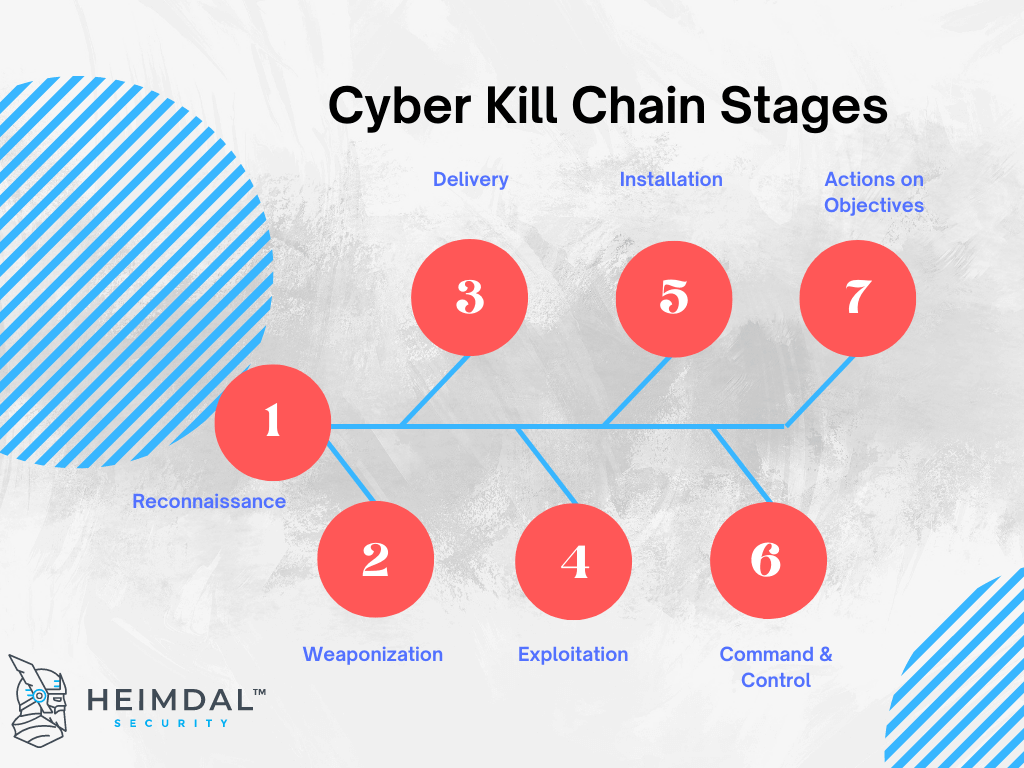
What Is Cyber Kill Chain Process Offensive And Defens Vrogue Co The cyber kill chain, also known as the cyberattack lifecycle, is a model developed by lockheed martin that describes the phases of a targeted cyberattack. it breaks down each stage of a malware. Key takeaways. the cyber kill chain is a cybersecurity model that breaks down a typical cyberattack into stages to help security teams identify in progress cyberattacks and stop them. the cyber kill chain includes eight phases: reconnaissance, weaponization, delivery, exploitation, installation, command and control, actions on objectives, and. In cybersecurity, the cyber kill chain is a model outlining the various phases of common cyberattacks. using the cyber kill chain, organizations can trace the stages of a cyberattack to better anticipate and prevent against cyber threats in the future. each stage of the cyber kill chain is related to a specific type of activity in a cyberattack. The cyber kill chain is a pivotal concept in cybersecurity, serving as a roadmap for understanding the sequential stages of a cyber attack. by dissecting an attack into distinct phases, from initial reconnaissance to the final objective, the model provides organizations with a structured framework to counteract threats at every step.
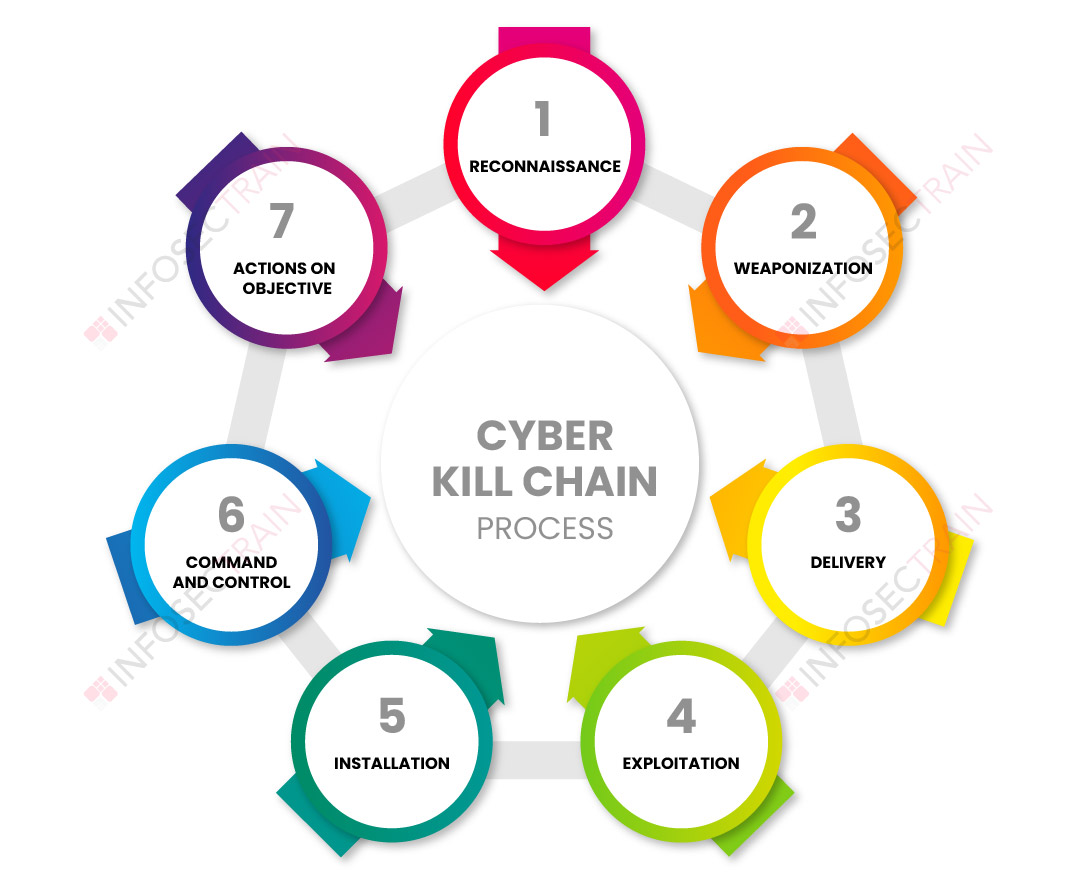
What Is The Cyber Kill Chain Process Infosectrain In cybersecurity, the cyber kill chain is a model outlining the various phases of common cyberattacks. using the cyber kill chain, organizations can trace the stages of a cyberattack to better anticipate and prevent against cyber threats in the future. each stage of the cyber kill chain is related to a specific type of activity in a cyberattack. The cyber kill chain is a pivotal concept in cybersecurity, serving as a roadmap for understanding the sequential stages of a cyber attack. by dissecting an attack into distinct phases, from initial reconnaissance to the final objective, the model provides organizations with a structured framework to counteract threats at every step. The cyber kill chain is the process by which perpetrators carry out cyberattacks. [2] lockheed martin adapted the concept of the kill chain from a military setting to information security, using it as a method for modeling intrusions on a computer network. [3] the cyber kill chain model has seen some adoption in the information security. If you’re responsible for defending a network, this model can help you understand the stages of a cyberattack and the measures you can take to prevent or intercept each step. the cyber kill chain is divided into seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control (c2), and actions on objectives.
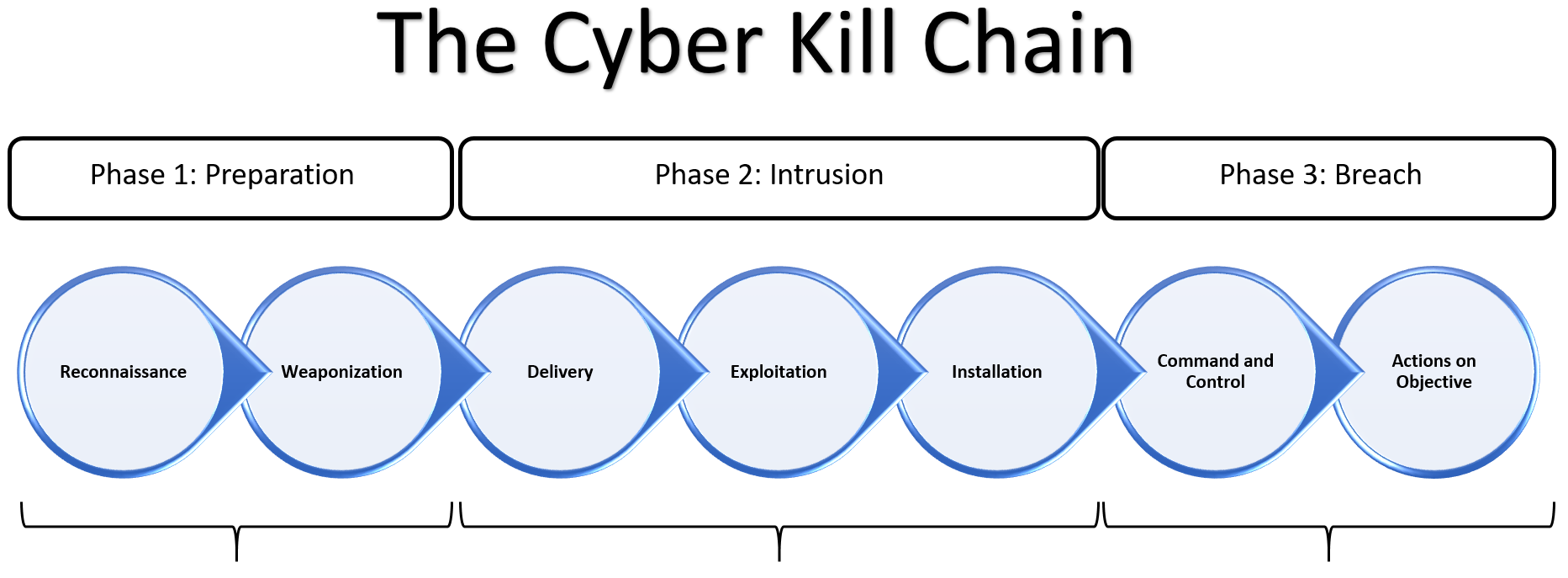
Understanding The Cyber Kill Chain Practical Cyber Intelligence Book The cyber kill chain is the process by which perpetrators carry out cyberattacks. [2] lockheed martin adapted the concept of the kill chain from a military setting to information security, using it as a method for modeling intrusions on a computer network. [3] the cyber kill chain model has seen some adoption in the information security. If you’re responsible for defending a network, this model can help you understand the stages of a cyberattack and the measures you can take to prevent or intercept each step. the cyber kill chain is divided into seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control (c2), and actions on objectives.

Comments are closed.