What Is Pretexting And How To Protect Yourself From It Samleopold
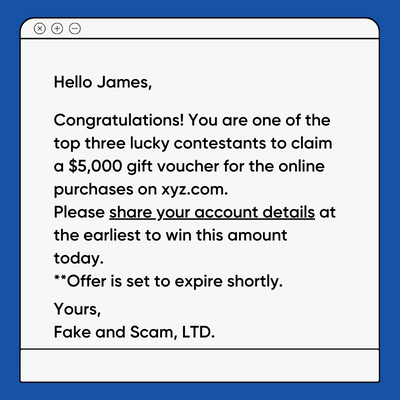
What Is Pretexting And How To Protect Yourself From It Samleopold Use the information protect! merely put, making pretense is making a scenario, usually with urgency, that lures you into offering essential info that you simply in any other case would not give. however that is extra sophisticated than only a random textual content message. Pretexting tactics usually involve a scammer playing a convincing character that’s used to develop a fake, but plausible, story that the victim can relate to. these stories tap into a victim’s emotions and suspend any suspicions they may have. pretexting scams can use social engineering tactics to take advantage of a victim’s emotions.
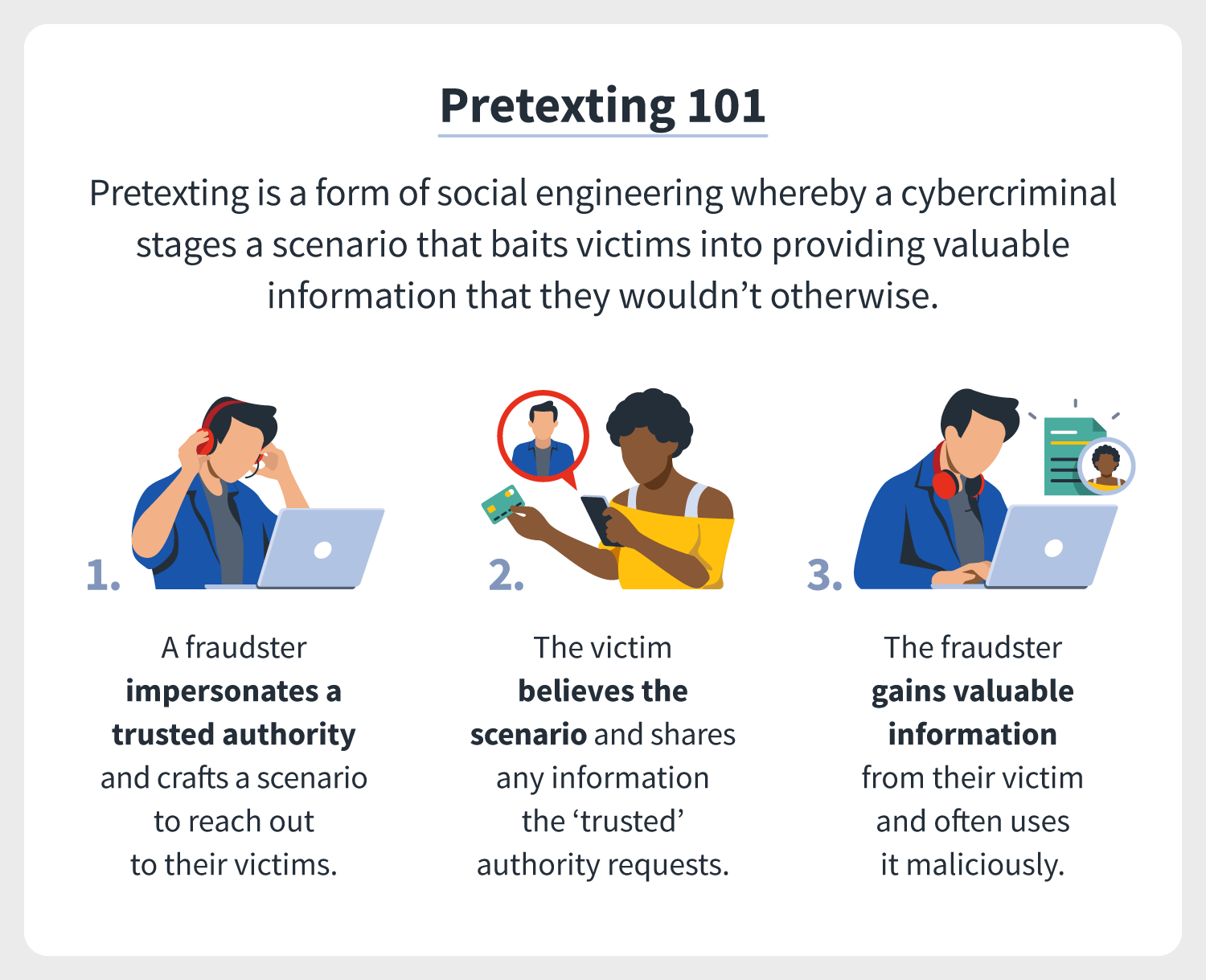
What Is Pretexting Definition Examples Prevention Tips Norton Pretexting is form of social engineering in which an attacker tries to convince a victim to give up valuable information or access to a service or system. the distinguishing feature of this kind. Pretexting is a type of social engineering attack that involves a criminal creating a story, or pretext, that manipulates their target into sharing personal data like passwords, credit cards, and logins. the attacker will come up with a scenario beforehand that seems believable and can exploit your trust in a person, company, or service. There are various pretexting techniques scammers and hackers use to gain access to sensitive information. 1. vishing and smishing. these techniques are very similar. vishing attacks involve using voice calls to persuade a victim to give up the information needed by the scammer. Below are a few specific examples of steps you can take to prevent an attack causing damage to you or your business. here’s how to avoid a pretexting attack: establish security protocols, policies, and procedures for handling sensitive information. do not divulge sensitive information to unverified entities via email, phone, or text messages.

Comments are closed.